From role activation to session control: Why PIM needs PAM

Matt Miller
November 24, 2025
Small and mid-sized teams face the same risks as enterprises—with fewer hands. The good news: you don’t need months or a massive budget to close your biggest gaps.
- Privileged Identity Management (PIM) controls who may become privileged, usually by activating roles for a limited time (often human identities).
- Privileged Access Management (PAM) governs how privileged access is used, covering credentials and sessions for both user and admin accounts.
They’re complementary: Keep PIM for role activation, add PAM to govern what happens during elevated work.
Where identity ends and privilege begins
Here’s the boundary in practical terms: PIM excels at who can become privileged, with features like just-in-time elevation, time-bound access approvals within your identity platform, MFA enforcement, and activation history. If your primary concern is granting a global admin role for a limited window, PIM is the right tool.
PAM extends control to how elevated access is used. Modern PAM goes beyond a password vault and governs access end-to-end. Here’s how:
- Vaulting & rotation (including rotate on check-in) of passwords to shrink reuse windows.
- Credential injection to launch RDP/SSH with no passwords accessed by the user.
- Time-boxed approvals with reason and ticket capture.
- Session recording that ties actions to requests.
- Discovery that brings unknown privileged accounts under policy (including from custom providers).
Together, these controls turn privileged access from ad-hoc exceptions into short, auditable events—fewer shared secrets, faster approvals with context, and sessions that end cleanly with automatic rotation.
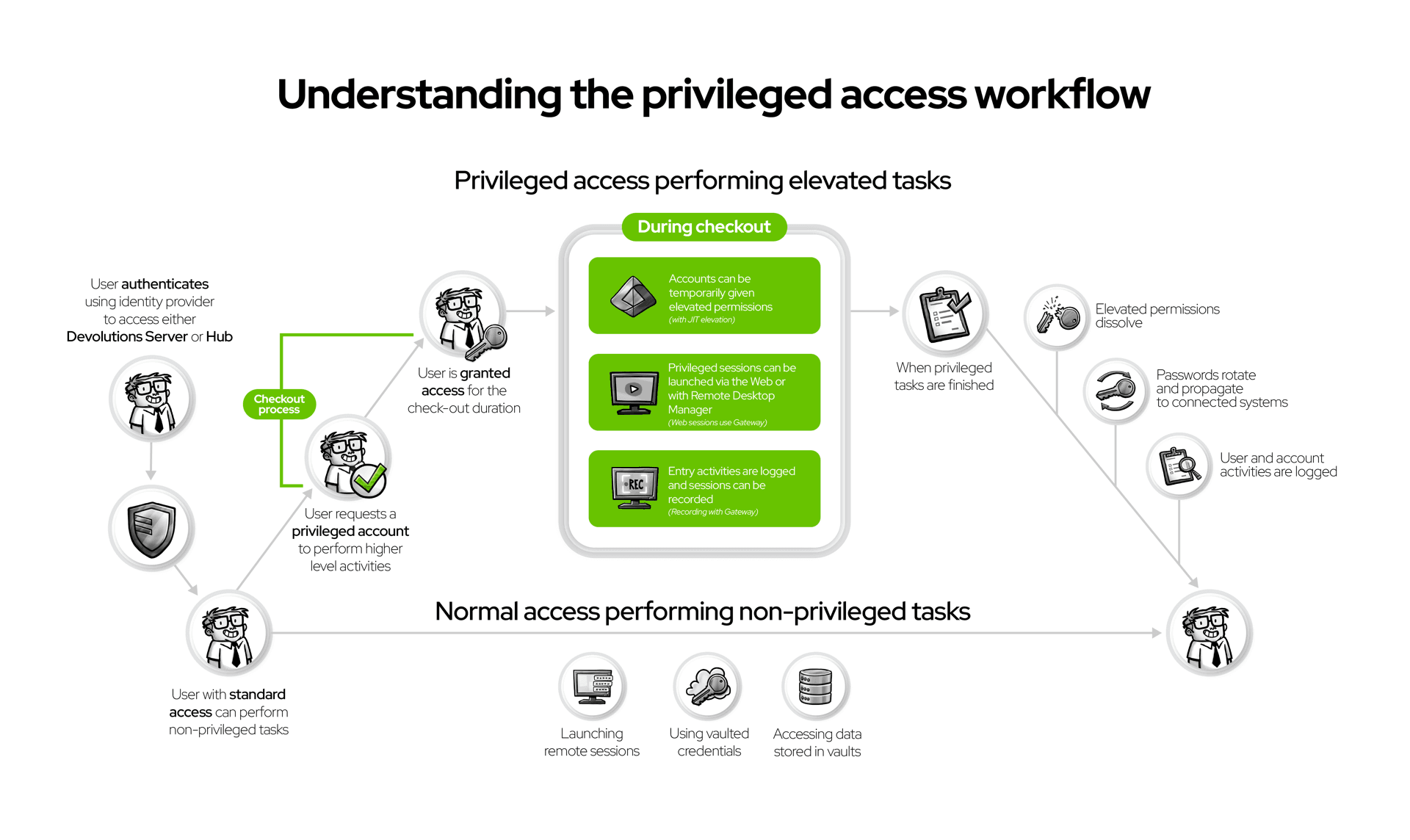
How it works in RDM (day to day)
With Remote Desktop Manager (RDM) as the centralized console and data source, admins don’t change tools:
- Access is requested (including a reason and/or ticket).
- An approver grants a time-boxed window.
- An RDP/SSH session is launched via Devolutions Gateway with credential injection (passwords aren’t revealed and “view password” rights can stay disabled).
- The session is recorded.
- On check-in, credentials rotate automatically.
The result: The same daily workflow—now governed, auditable, and short-lived.
Get started with PAM—in hours, not months
Choose Devolutions Hub (cloud-hosted) or Devolutions Server (self-hosted). Connect a provider, then:
- Identify 5–10 high-risk accounts with the privileged account discovery feature.
- Vault them with password rotation after use, or on a schedule.
- Control access with roles and time-boxed approvals.
- Record sessions (RDP/SSH) for accountability.
- Conduct discovery regularly so new accounts are pulled into policy.
Stand up protections fast, with measurable results from day one.
How IT teams teams feel the difference
- Less complexity, more ergonomics: A user-friendly path that works for remote staff and segmented networks—without heavy infrastructure or constant context switching.
- Coverage beyond roles: Day-to-day work touches local accounts, servers, service accounts, databases, devices, and more. PAM gives those the same guardrails—vaulting, rotation, approvals, recording—not just role activation.
- Operational hygiene built-in: Simple check-outs, automatic resets, and easy account imports keep operations moving without ad hoc exceptions.
- Time to value: Stand up core controls quickly, then expand discovery weekly so new accounts are pulled under policy as they appear.
- Best pricing in the market: Predictable costs without enterprise overhead.
The takeaway: Pair PIM + PAM for full coverage.
- Use PIM to control who can activate roles in your identity platform for a limited time.
- Use PAM to control how elevated access is used across your estate—credentials vaulted and rotated, access approved and time-boxed, sessions recorded, no passwords on screen.
Together, you get identity, intent, and accountability—the full story auditors and incident responders expect.
Try it in your environment
Pair your identity platform with Devolutions PAM to govern elevated work. Stand up discovery, vaulting & rotation, time-boxed approvals, and session recording in hours on Devolutions Hub or Devolutions Server. Run the flow in RDM, confirm it fits your day-to-day, and scale on your terms—with the best pricing in the market.
