Introducing new DevOps integrations in the Devolutions integration center: Ansible, Kubernetes, and Terraform

Marc Beausejour
January 14, 2026
The Devolutions integration center now lists three of the most widely used DevOps tools: Ansible, Kubernetes, and Terraform. These integrations support both open-source and enterprise workflows, making it easier to automate infrastructure, manage infrastructure as code, and secure sensitive data across environments.
By pulling credentials directly from Devolutions Server, teams can standardize provisioning, configuration management, and application deployment while keeping secrets centralized and out of configuration files and source repositories.
This gives DevOps teams a unified approach to secure access, runtime credential injection, and deploying and managing modern infrastructure. You can use the same centralized vault across CI/CD pipelines, orchestration platforms, and infrastructure-as-code workflows, whether you are working with virtual machines, containerized applications, or public cloud services.
Why connect DevOps workflows to the Devolutions ecosystem?
DevOps teams often struggle with secrets spread across vault files, repository variables, cloud key stores, and encrypted configuration files. This fragmentation increases risk and complicates deploying and managing infrastructure across data centers and public cloud environments.
By connecting DevOps workflows to Devolutions Server, you gain:
- A centralized secrets vault for automation and remote connections
- Role-based secure access to limit who can retrieve production credentials
- Automatic audit logs for every secret request
- Dynamic, just-in-time credential retrieval aligned with desired state operations
- Reduced exposure of sensitive data in local files
This approach strengthens security while simplifying provisioning, configuration management, and application deployment across CI/CD, GitOps, and hybrid infrastructure.
Ansible integration: secure, dynamic secrets for automation
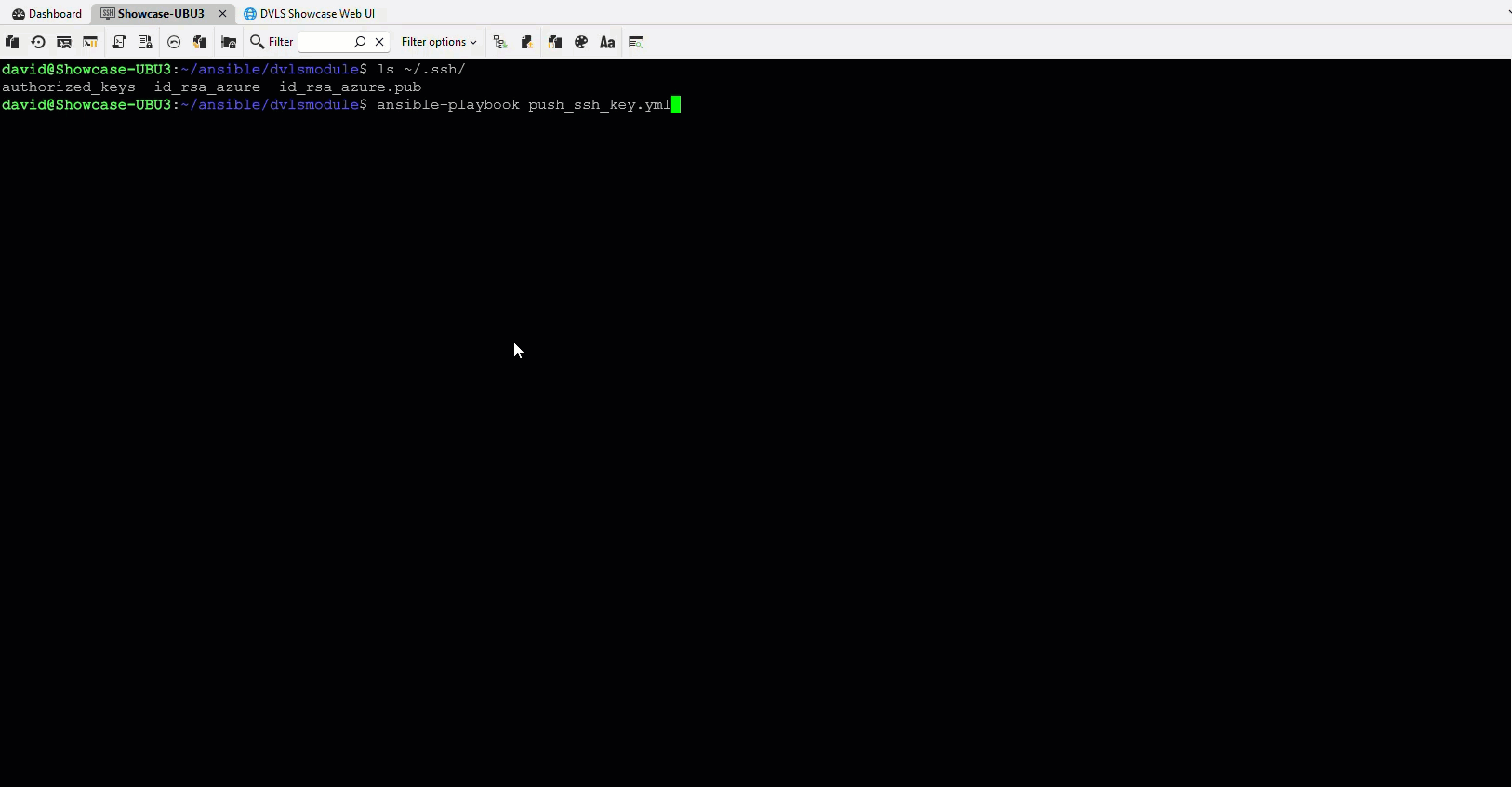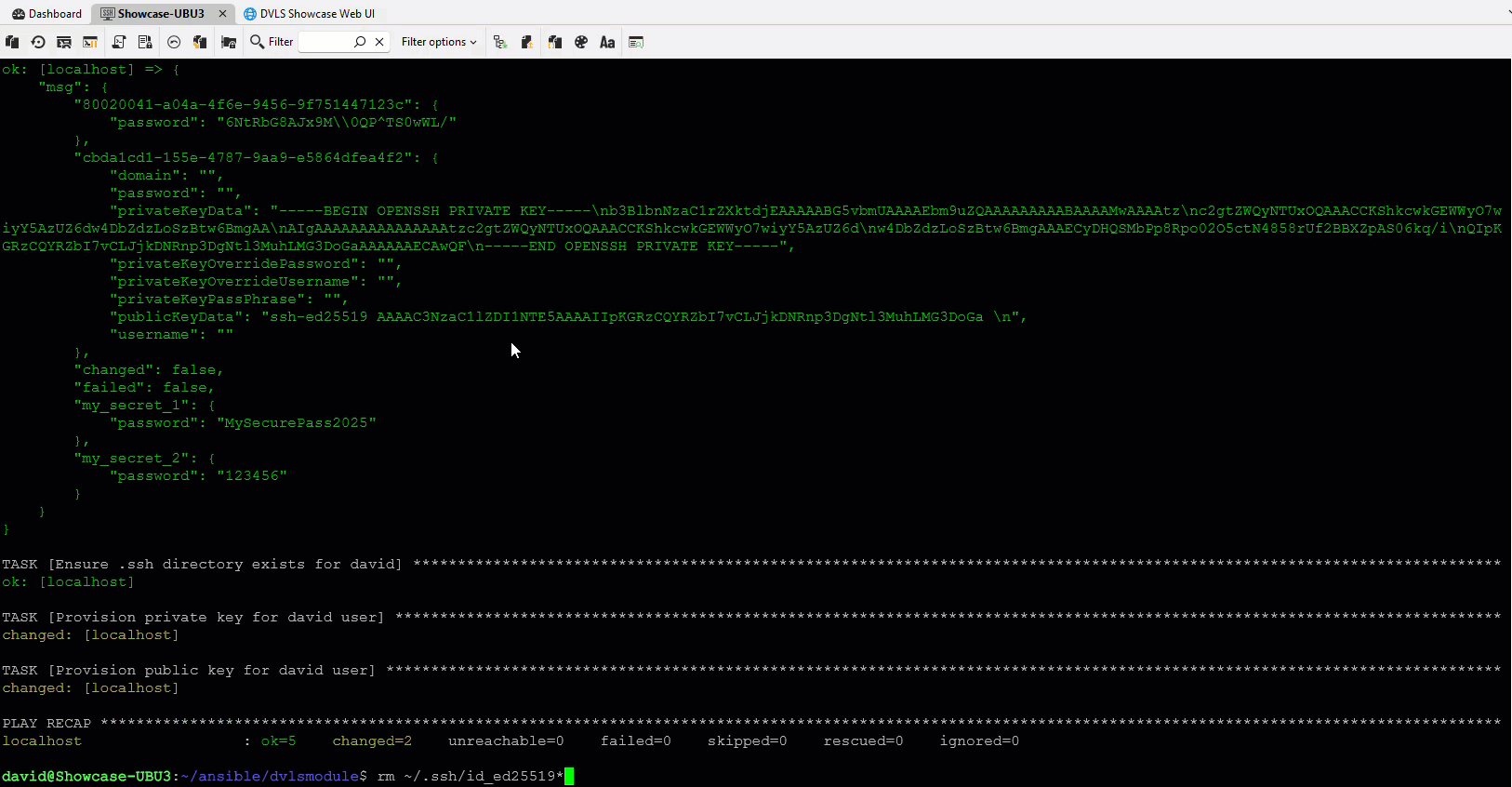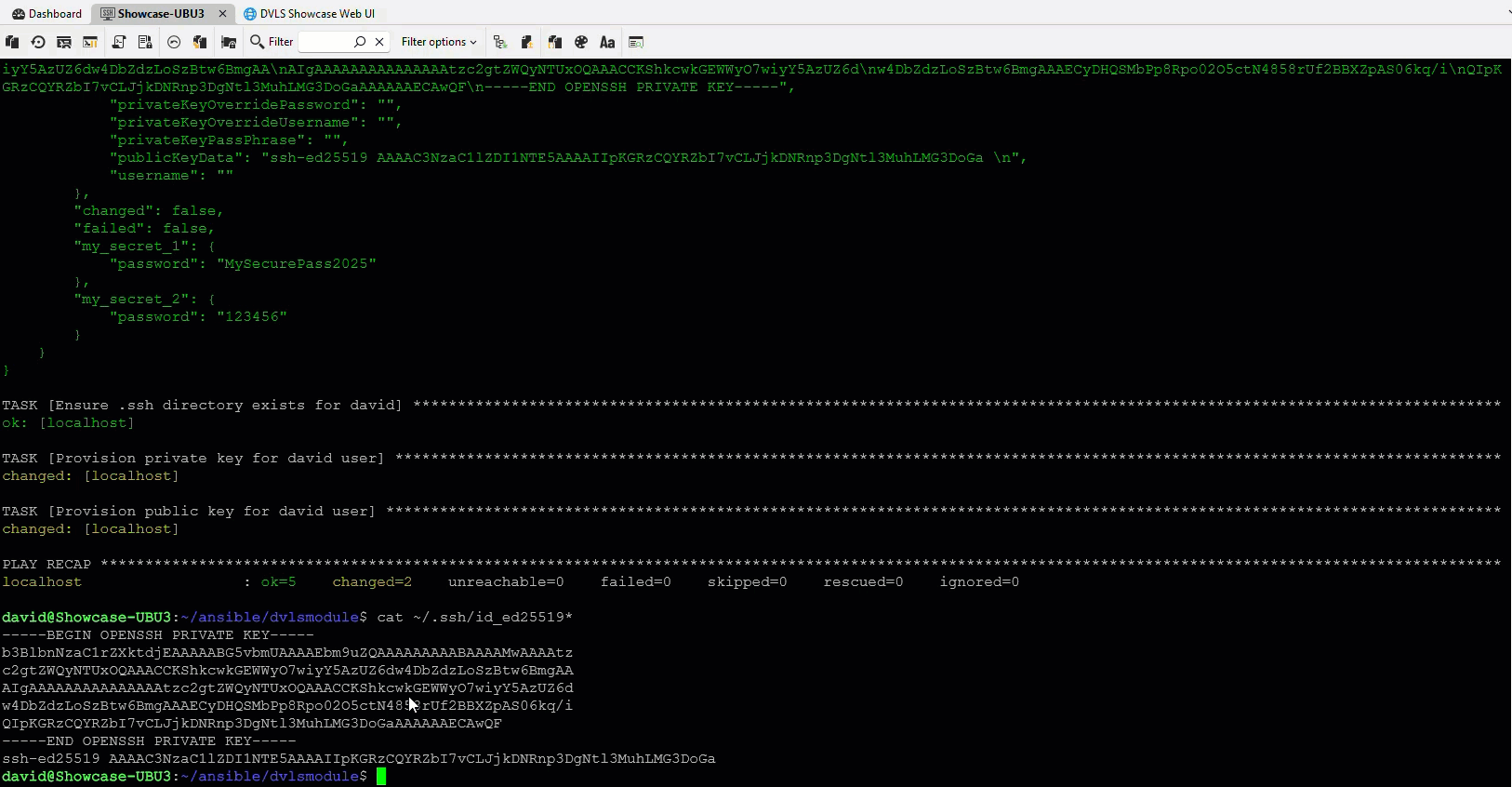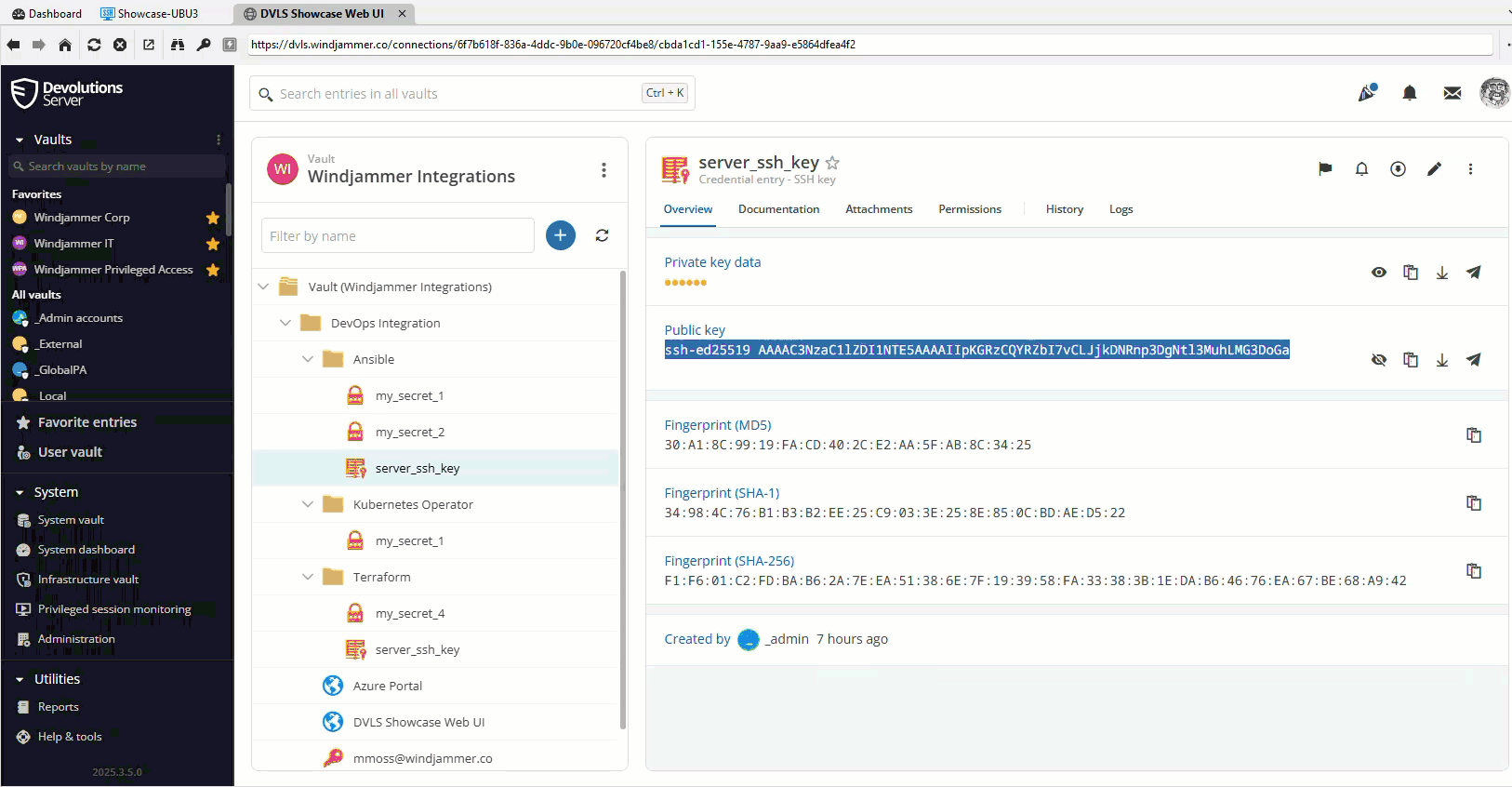
The Ansible integration lets an Ansible playbook request secrets directly from Devolutions Server at runtime. This removes the need for Ansible Vault, encrypted files, or static variables stored in a configuration file.
Use cases
Eliminate Ansible Vault management
No more vault passwords, re-encryption, or juggling multiple encrypted files. Playbooks retrieve secrets securely during execution.
Dynamic secrets provisioning for CI/CD
Provision infrastructure and applications without writing credentials to disk, logs, or state files. Secrets remain centralized and protected.
Credential rotation without code changes
When credentials rotate in Devolutions Server, Ansible automatically uses the new values with no playbook updates required.
Role-based secret access across environments
The same Ansible playbook can run in dev, staging, or production while Devolutions enforces access based on environment and resource requirements.
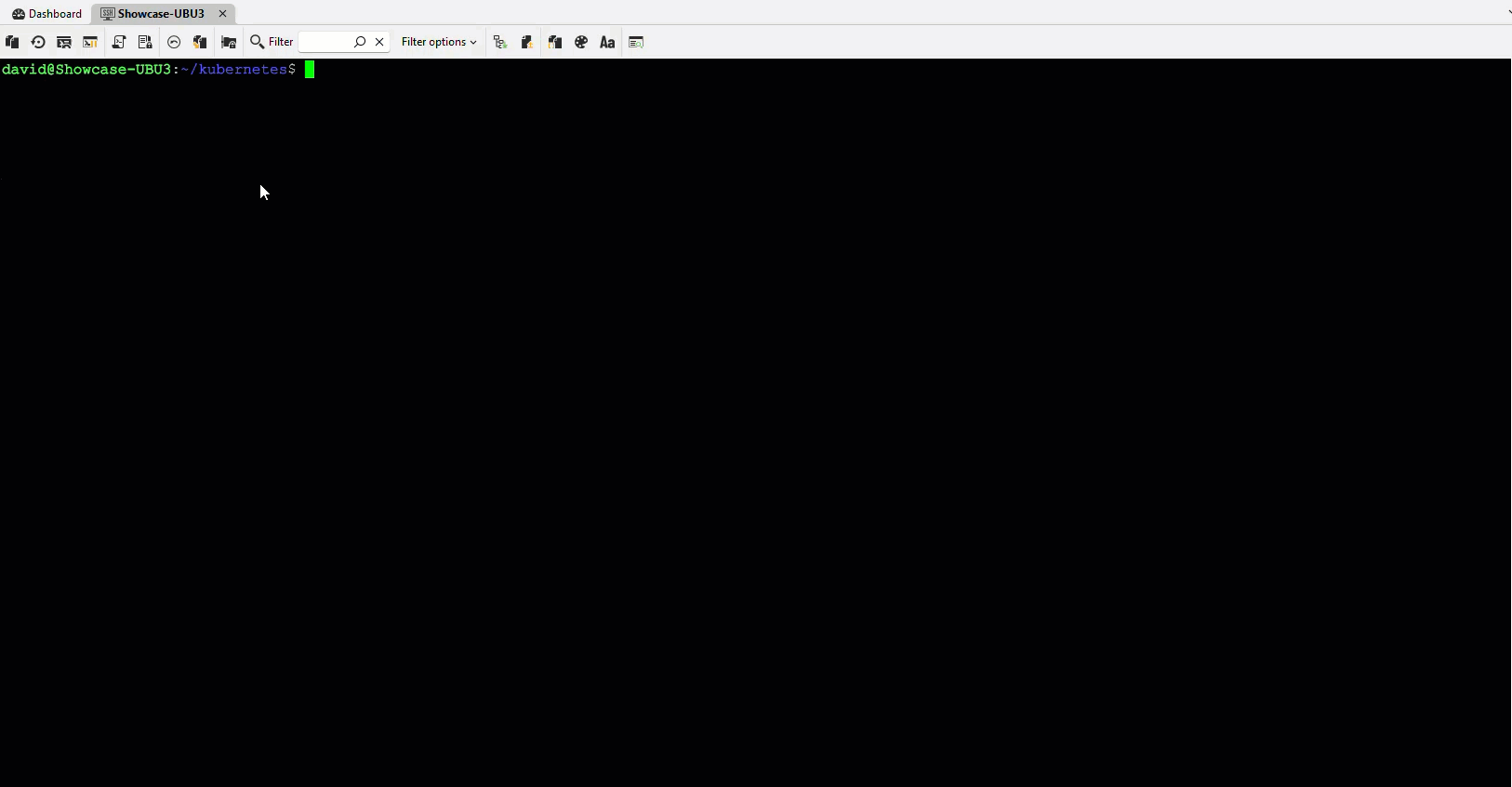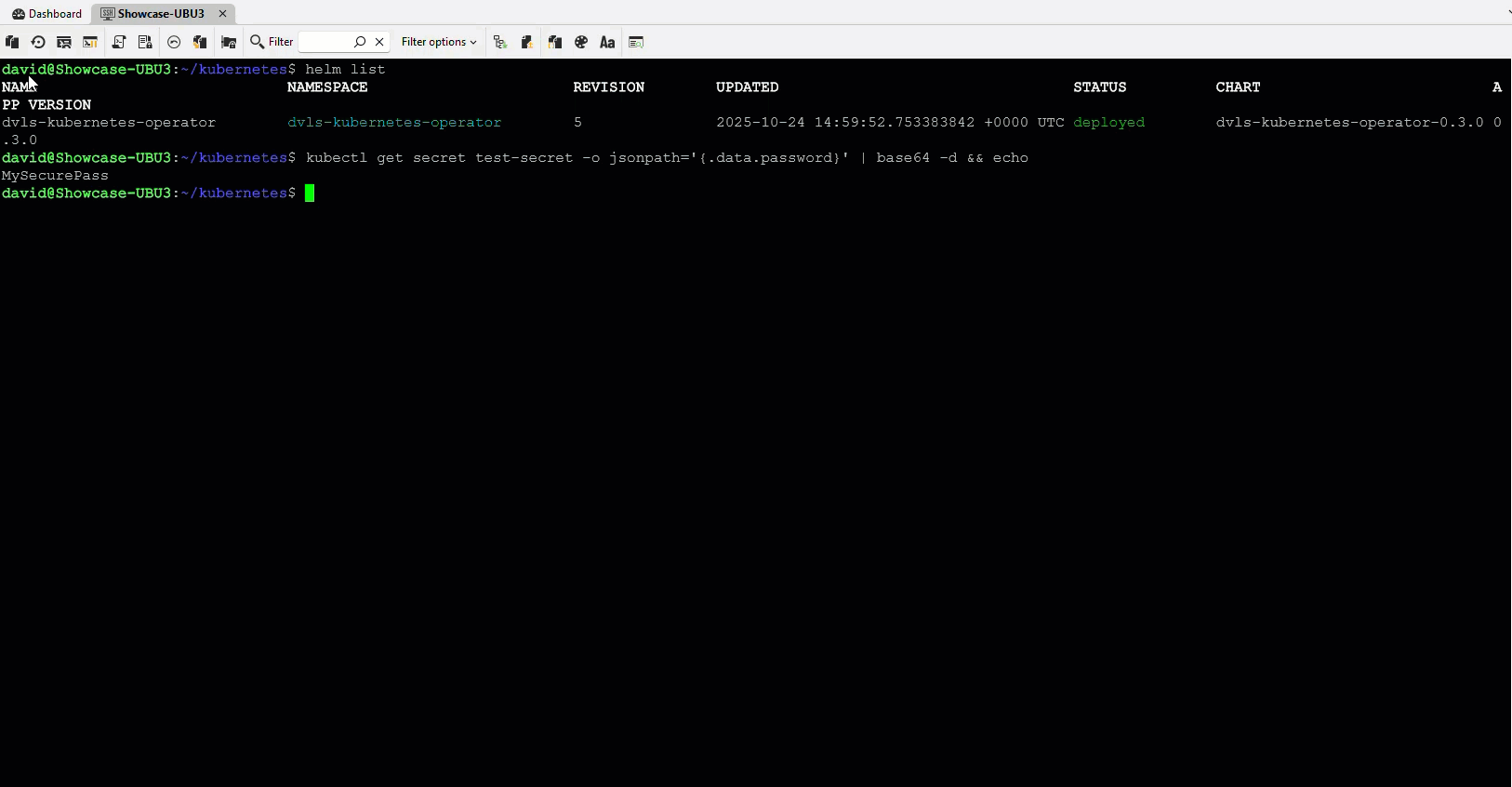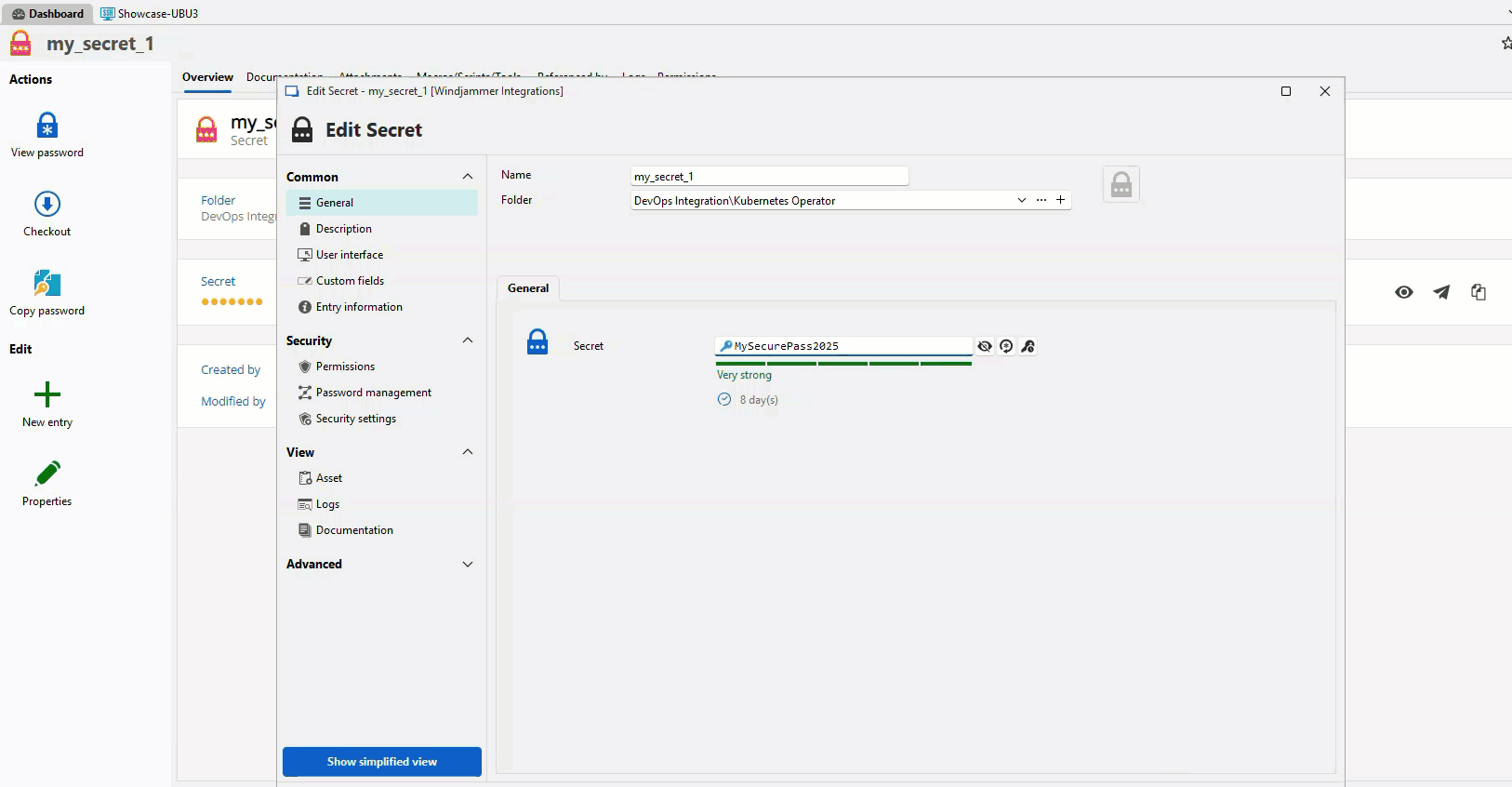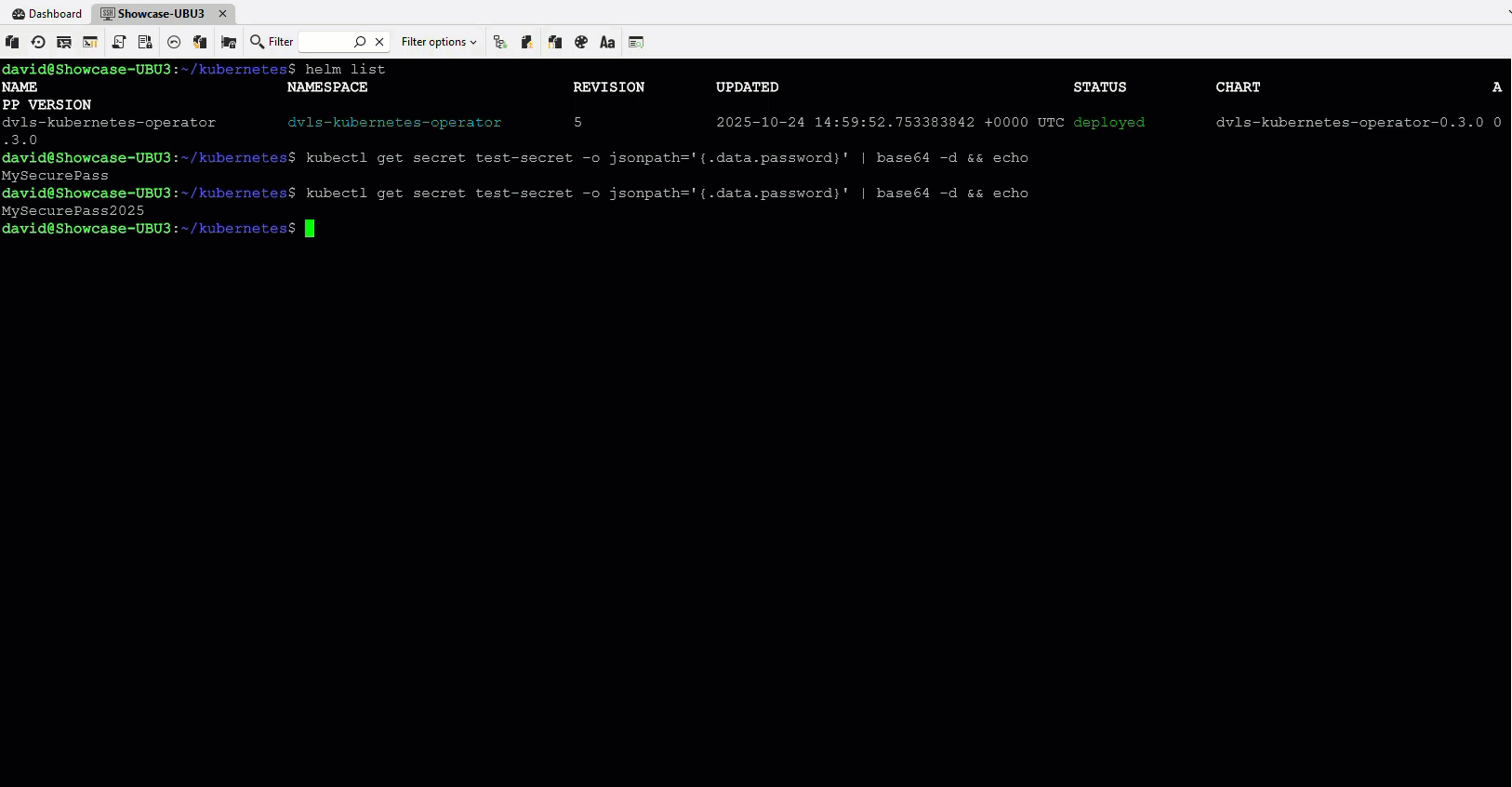
Kubernetes integration: GitOps-safe and centralized secret management
The Kubernetes integration introduces a DvlsSecret custom resource. This lets clusters pull secrets directly from Devolutions Server without placing them in manifests, ConfigMaps, or Helm charts.
Use cases
Remove secrets from Helm charts and manifests
Deploy applications using DvlsSecret references instead of embedding sensitive data in YAML or templates.
Centralized multi-cluster secret management
Manage secrets for all clusters from a single vault, instead of maintaining separate stores per cluster or namespace.
GitOps-friendly secrets
Store DvlsSecret CRDs in Git while the real credentials remain in Devolutions Server. This keeps repos clean and safe, even when public.
Environment-specific secret injection
Use the same manifests for dev, staging, and production. Kubernetes retrieves the correct secrets from the matching Devolutions Server vault.
Simplified cluster recovery
If you rebuild a cluster from GitOps, the operator automatically restores all secrets from Devolutions Server without manual steps.
Terraform integration: secure secrets for Infrastructure as Code
With the Terraform integration, modules and configurations can retrieve credentials directly from Devolutions Server instead of embedding secret variables in code, repositories, or module inputs.
Use cases
Dynamic database and application credentials
Pull RDS passwords, connection strings, and application secrets from Devolutions Server during terraform operations.
Environment-aware secret injection
Use the same Terraform code across dev, staging, and production by pointing to different vaults based on workspace or variables.
SSH key distribution for provisioned machines
Fetch and deploy SSH keys from Devolutions Server when creating new virtual machines.
Centralized API tokens and service accounts
Populate Kubernetes secrets or application configs using tokens, certificates, and service accounts managed in Devolutions Server.
Eliminate sensitive module inputs
Reusable modules can query Devolutions Server directly, removing the need to pass sensitive variables through module interfaces.
Certificate and key material deployment
Retrieve SSL certificates, private keys, and CA bundles from Devolutions Server to configure load balancers, gateways, and ingress controllers.
Start using the new DevOps integrations today!
These Ansible, Kubernetes, and Terraform integrations are available in Devolutions Server today. They provide a secure and consistent way to manage secrets across infrastructure as code, application deployment, CI/CD pipelines, and containerized applications.
These integrations are evolving progressively, and we are still in the early stages of development. Your feedback and feature requests are highly appreciated.
If you want help testing or rolling out these integrations across your environments, our team is ready to assist!