Spotlight on: just-in-time provisioning vs. just-in-time elevation

Matt Miller
January 26, 2026
Privileged access is the “keys to the kingdom.” Once attackers get valid credentials with elevated rights, perimeter defenses and multi-factor authentication (MFA) alone aren't enough, especially in environments where privileged accounts have quietly accumulated rights over years of quick fixes and emergency work. For modern IT teams, Zero Standing Privilege (ZSP) and the Principle of Least Privilege (PoLP) are essentials for security and compliance.
Just-in-time (JIT) is at the heart of making ZSP practical. In this article we’re looking at two complementary approaches, JIT elevation and JIT provisioning, and how Devolutions PAM helps you use both to shrink the attack surface without slowing your team down.
Just-in-time elevation: Temporarily boosting an existing account
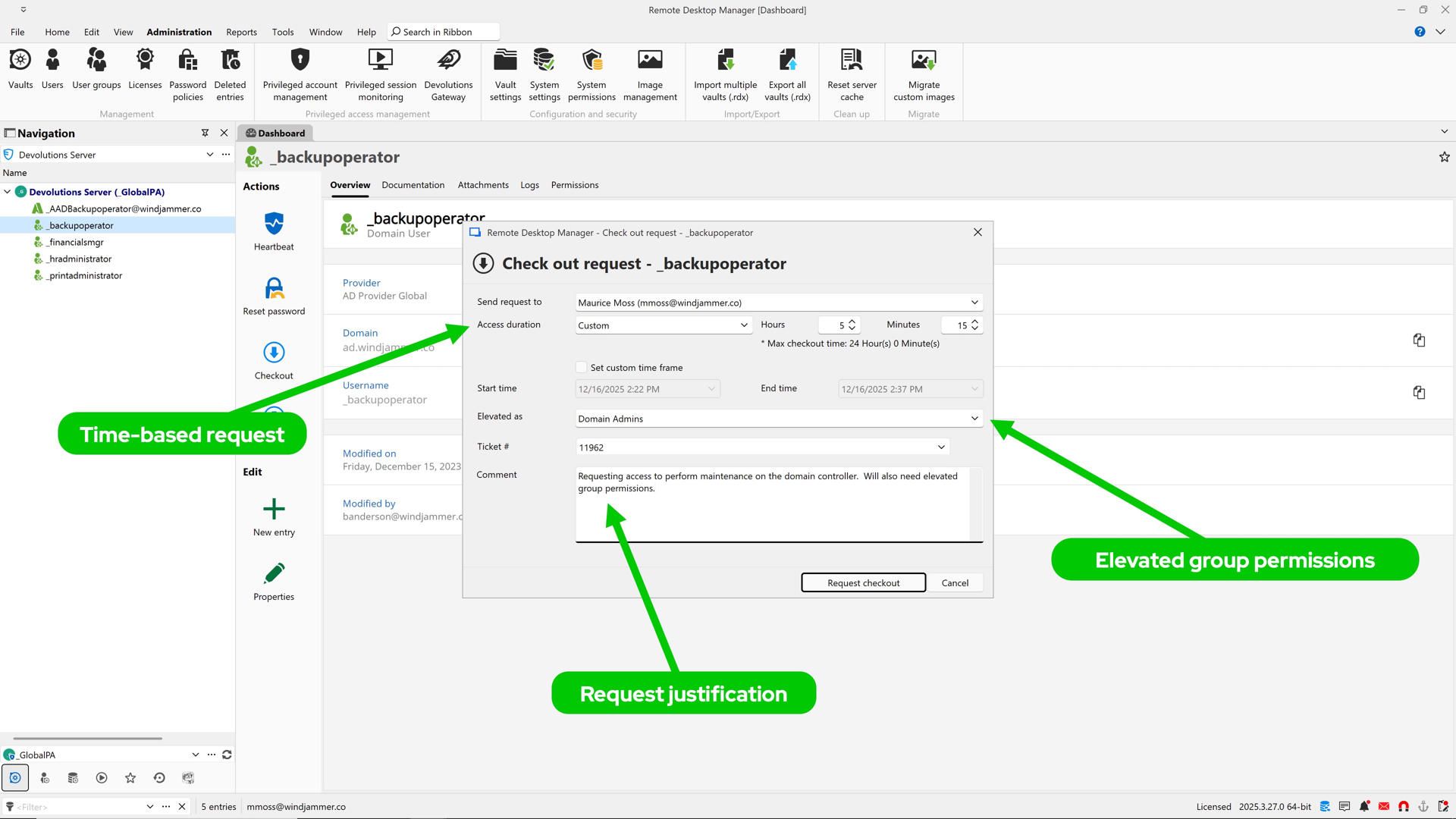
JIT elevation lets you grant elevated permissions to an existing user account only when it's needed, and only for as long as it's necessary. Instead of giving admins broad, always-on rights, you temporarily “turn up” their permissions for a specific task, then automatically return them to baseline when that task is complete. This stops privilege creep and limits exposure of sensitive permissions.
With Devolutions PAM, JIT elevation typically works by dynamically adjusting group memberships or role assignments in Active Directory or Entra ID (Azure AD):
- A user requests access to perform a privileged task.
- An approval workflow is triggered.
- At checkout, Devolutions PAM temporarily adds the account to the required groups or roles.
- At check-in, elevated credentials or roles are automatically revoked.
This supports both mid-level accounts that occasionally need more rights and ZSP-style accounts that have no privileges at rest and gain everything via JIT elevation.
Want to see how it works in your own environment?
Start a 30-day PAM trial and test JIT Elevation and JIT Provisioning in the Devolutions ecosystem.

Just-in-time provisioning: Disposable privileged accounts
JIT provisioning goes a step further. Instead of elevating an existing account, it creates a brand-new, temporary privileged account for the task at hand — and then removes it when the task is done. This drastically reduces the risk of forgotten or dormant admin accounts that linger in your directory.
With Devolutions PAM:
- At checkout, a new account (for example, in Active Directory) is created with the exact permissions you’ve defined.
- The account exists only for the approved checkout window.
- At check-in, the account is removed from the directory.
You can enable this behavior by configuring the appropriate PAM Provider and selecting the “Just-In-Time (JIT) account” option when adding a new user entry in the PAM Vault, so provisioning and cleanup are automatic and fully audited.
Elevation vs. provisioning: Key differences and when to use each
Even though both strategies eliminate permanent access, they control different pieces of the puzzle.
Think of JIT elevation as lending a coworker a “super keycard” for three hours, then removing its extra door access. The card still exists. JIT provisioning is like printing a single-use keycard for one job and shredding it afterward. Nothing is left behind.
| Focus of control | Standing risk | |
|---|---|---|
| JIT elevation | The account is permanent; the privileges are temporary | Removes standing admin rights, but the base account remains |
| JIT provisioning | The account is temporary; privileges are temporary | Removes both standing privileges and standing privileged identities for that task |
Enhancing security and compliance with Devolutions PAM
By combining JIT elevation and JIT provisioning, IT teams in SMBs and MSPs can enforce the Principle of Least Privilege (PoLP) and Zero Standing Privilege (ZSP) in a way that fits real-world operations: less standing risk, more control, and fewer compromises between agility and security. Limiting how long privileged accounts and permissions exist also helps organizations align with security frameworks such as NIST, SOC 2, and ISO/IEC 27001, and with increasingly strict cyber insurance requirements.
Devolutions PAM, available in cloud-hosted and self-hosted deployments, delivers a unified privileged access workflow. Whether you're granting temporary rights to a known operator or creating a temporary privileged account for a high-risk task, Devolutions PAM can ensure every privileged action is controlled, audited, and temporary.
Start a free 30-day PAM trial or try Devolutions PAM in a free, browser-based lab session to see how we’re helping IT pros achieve great PAM coverage with less standing access in their organizations.
