What's New in Remote Desktop Manager 2023.2
Greetings! We’re delighted to announce that Remote Desktop Manager 2023.2 is now available. This is the second major update this year, and many of the additions and improvements are the result of feedback from members of our global user community.
- New features:
- User Interface Profiles
- Link Two User Accounts to the Same License
- Request Access to Other Vaults
- System Vault for Globally Shared Resources
- Unix Terminal (LUSH)
- SSH Key Dashboard
- Access Code Credential Entry Type
- Improvements:
- Active Directory Console
- Network Scan
- Temporary Access Functionality
If you want to see the full and very long list of changes, please see the release notes.
New User Experience and User Management Features in Remote Desktop Manager 2023.2
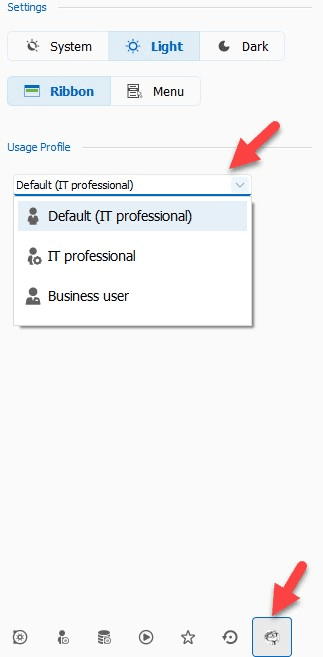
User Interface Profiles
To make things simpler and more efficient for both Administrators and non-technical users, we have created two new user interface profiles: IT Professional and Business User.
IT Professional: This is the default profile (and will look familiar!), which displays all entry types, options, and advanced properties. Please note that when it comes to security and governance, simply giving a user the IT Professional profile will NOT instantly give them access to everything. They must first have permission. Any unauthorized entry type/option will remain invisible and inaccessible.
Business User: This is a new profile type specifically designed for users who do not need to see all remote connection entries, administrative options, and advanced properties. This more streamlined interface lets users focus on their daily tasks and information requirements, without having to see extra details that are not relevant to them.
Link Two User Accounts to the Same License
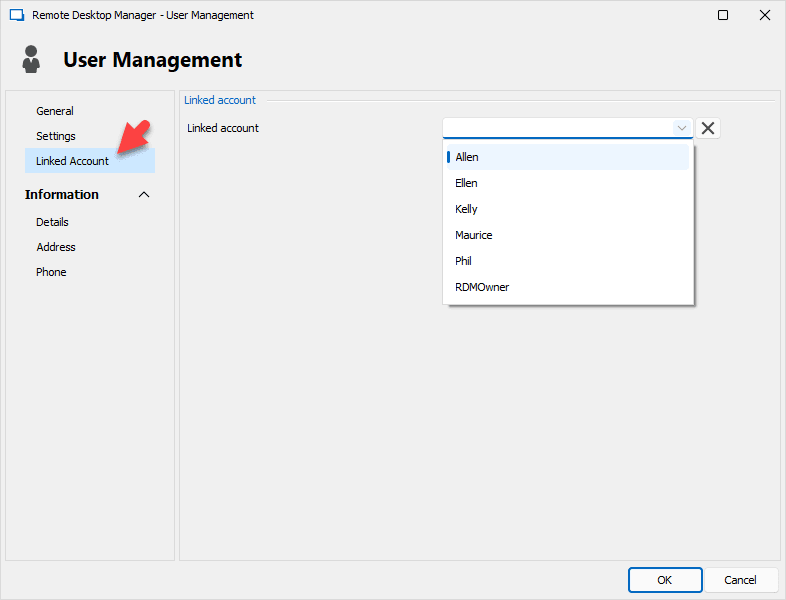
In the past, some Remote Desktop Manager users were obliged to create two separate accounts in order to enable two types of users: a regular user with normal permission for typical day-to-day tasks, and a “super user” with elevated permission for privileged tasks.
Yes, we said “in the past,” because we are delighted to announce that in version 2023.2 we have eliminated this requirement! Now, users can link BOTH of their accounts to a SINGLE license. Thank you to all users who wanted to see this improvement. As we say around here: your wish is our command!
Click here to learn more about how to link accounts in Remote Desktop Manager.
Request Access to Other Vaults
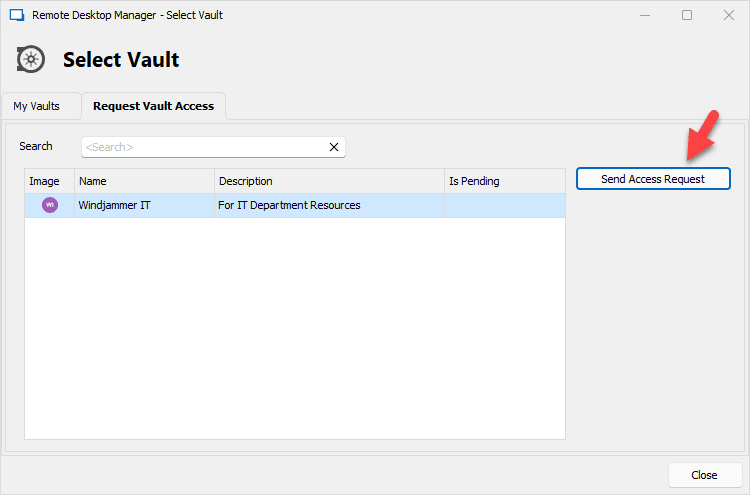
Previously, users who did not specifically have permission to access a publicly shared vault would not see it in their dropdown list. Now in v2023.2, they will see these publicly shared vaults (see note below), and can request access.
Once the request is sent, a Vault Owner or Administrator is notified, and can approve/deny the request. Click here to learn more about this workflow.
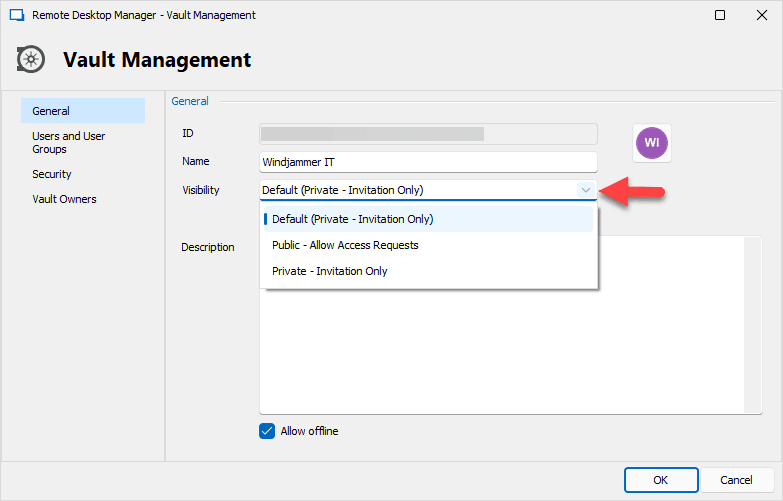
Note: By default, all vaults are set to private. In order to make a vault publicly shared, the Administrator must toggle this in the new Vault Visibility option. Also, please remember that simply changing a private vault into a publicly shared vault will NOT instantly give all users access, even if they can see the vault in their dropdown list. As mentioned above, in order to gain access a user must have their request granted.
System Vault for Globally Shared Resources
To centralize commonly used resources (macros, VPNs, and contacts), we have introduced a new vault called the System Vault. It is no longer necessary to populate multiple shared/individual vaults with the same resources. Just drop them into the System Vault, choose which shared/individual vaults can access them, and voilà: you’re done!
The System Vault works alongside the (current) Shared Vaults and User Vaults. This new feature is accessible in the View tab, or at the bottom of the navigation pane.

Unix Terminal (LUSH)
The Unix Terminal is a new entry designed to provide a native UNIX environment experience in Remote Desktop Manager. Based on FreeBSD, this addition extends the capabilities of terminal connections. Plus, there is no need to install Cygwin or Windows Subsystem for Linux (WSL). You can try it now by going to the Remote Management category when you add a new entry.

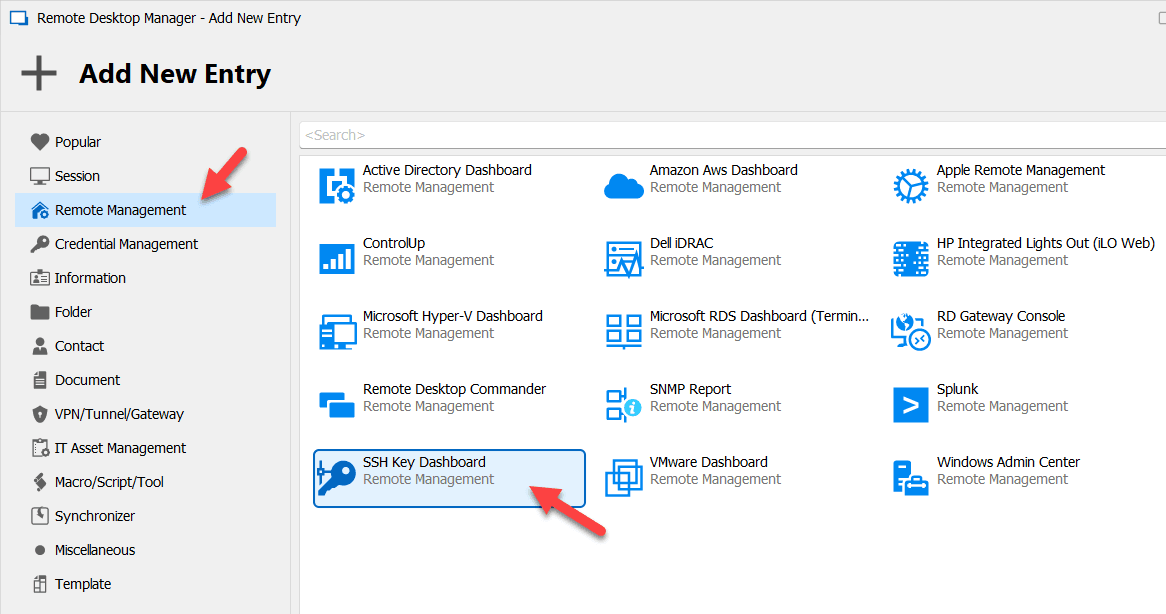
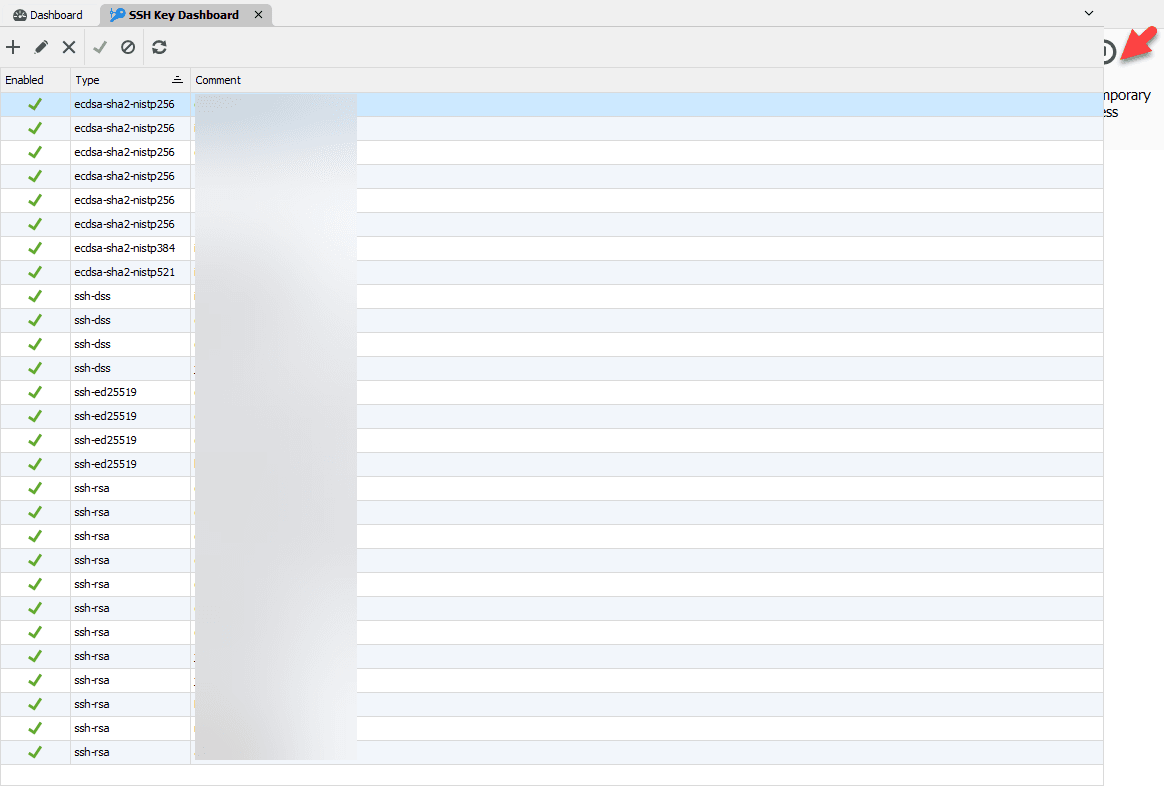
SSH Key Dashboard
We have added a new entry type to manage SSH public keys authorized on a server. Previously, it was necessary to manually modify an authorization file. This new entry simplifies access, and eliminates this administrative burden by providing a management interface for these keys. Simply open the Add New Entry menu and click Remote Management to find this new addition.
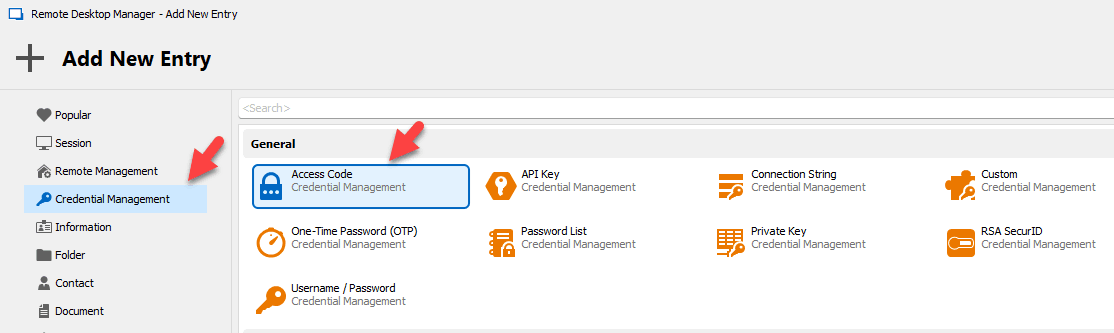
Access Code Credential Entry Type
We have added a new type of credential that is designed to contain a singular password. This simplifies the UI for users who can now copy their password to the clipboard with just one action button. The new access code credential entry type is found Credential Management when adding a new entry.
Feature Enhancements in Remote Desktop Manager 2023.2
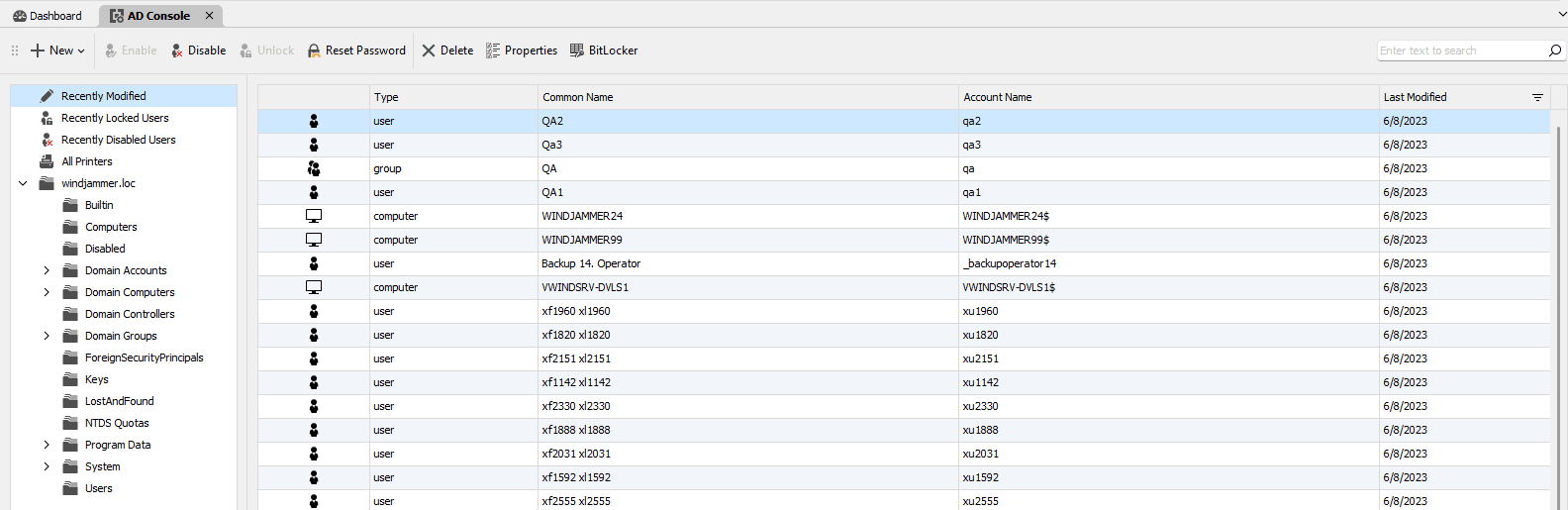
Active Directory Console
We have made several improvements to the AD console:
- Redesigned the UI to include AD tree structure by default.
- Queries are now included by default for “Recently Locked User”, “Recently Modified”, “Recently Disabled.”
- Added an icon that indicates if a user is locked or disabled.
- Improved the button design to unlock, enable/disable, and reset passwords.
- Added a new universal search box, which searches all objects in the domain.
- Added a “New User” and “New Group” function.
- Added a BitLocker key search function.
- Added a group-editing option, as well as the ability to modify group members.
- Added a “delete” option for all objects.
- Added “properties” for all types of objects.
Network Scan
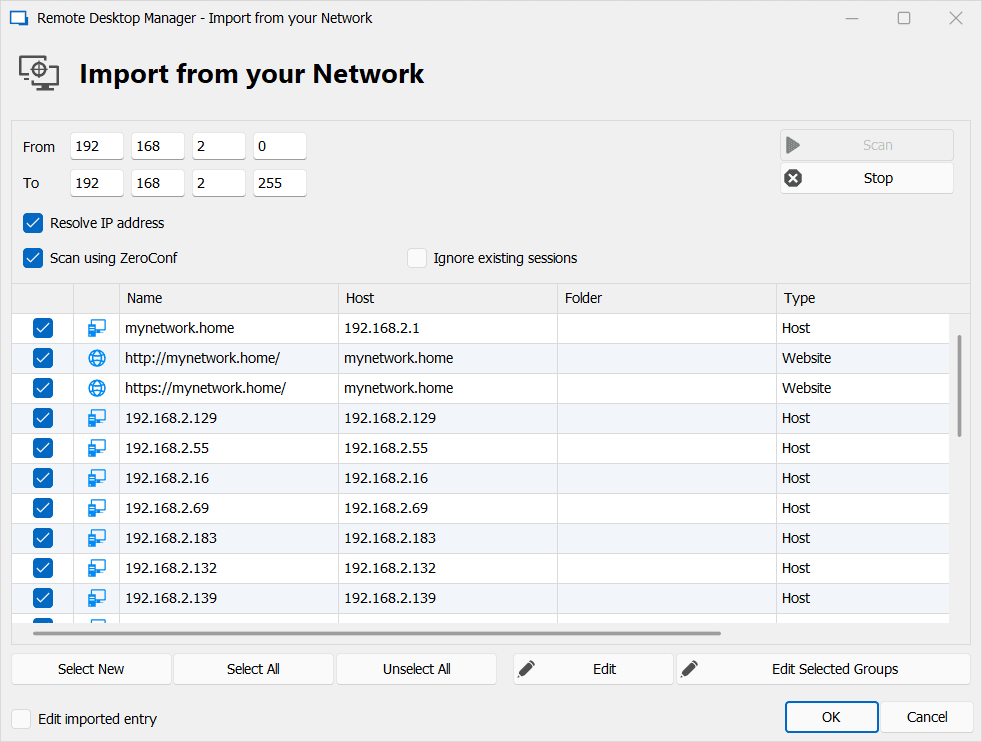
We have made some significant improvements to Remote Desktop Manager’s Network Scan tool:
- Added a broadcast Ping and reading ARP table to quickly discover servers .
- Implemented extensive subnet ping on all systems in subnet, threaded.
- Added ZeroConf (bonjour/mdns) scan to quickly discover systems.
- Improved specifying the subnet From-To range, which allows larger subnets than only the last 255 (see screenshot below).
- Added auto-detect for the current network subnet range of the system, instead of 127.0.0.1.
- Added Network Scan as a standalone function in the Tools tab (see screenshot below).
Temporary Access Functionality
We have enhanced how temporary access operates in Remote Desktop Manager (as well as our other main solutions, Devolutions Server and Devolutions Hub Business). Here is a summary of the major improvements:
-
Now when a user requests access to an entry with related dependencies (such as VPN or credentials), if the request is approved then all associated entries will be automatically granted at the same time. This eliminates the need for users to request each item individually, which streamlines the process for both users and Administrators.
-
Previously, users had to trigger the process by making a request. Now, Administrators can unilaterally grant temporary access, without requiring a request. This should make things more efficient for Administrators, plus they don’t have to wait around (or chase around!) users to make their request. Users can now request temporary access for a specific date/time range in the future. If approved, they will gain access to the entry during that period. There are several benefits of this improvement:
-
Users can send in their request as soon as they know that they need access, even if that is hours, days, weeks, or possibly months in the future. This reduces the chance that they will forget to do this, and will be forced to scramble at the last minute when they need to get their work done but do not have the required access!
-
Users no longer have to worry about Administrators not being immediately or imminently available when they submit their request. For example, if a user needs temporary access next Monday morning at 7:30 a.m., then it doesn’t matter if the Administrator starts work at 9:00 a.m. The user can make the request right now, which gives the Administrator ample time to review and approve.
-
Users can specify in their request if they need more time than is normally granted. For example, let’s say that in an Administrator’s experience, a temporary access request for a specific entry, by a user with a specific role/job title, should be granted for 15 minutes. However, on this occasion a user needs 30 minutes instead of 15 minutes, because they will be doing some additional and non-typical work. In this case, the user simply requests temporary access for 30 minutes, and sends a brief message explaining why they need more time. This is a much more efficient process for everyone.