Why SMBs need PAM that just works

Matt Miller
November 03, 2025
Why PAM is a priority—even for SMBs
Let’s be honest: traditional security programs are often built for big budgets and big teams. But that’s exactly why PAM can deliver such outsized value for SMBs.
By securing privileged accounts—those with the power to change configurations, access production data, or manage networks—you can reduce your attack surface fast.
A few small changes make a huge impact:
- Safeguard shared or static admin passwords with centralized rotation.
- Discover unknown privileged accounts hiding in your systems.
- Replace informal “just this once” access with approved, time-boxed requests that auto-expire and trigger credential rotation.
- Record or shadow privileged sessions so you can reconstruct what happened if something goes wrong.
Together, these steps improve audit readiness and incident response without rebuilding your entire IAM stack. Start small, prove it fast, then expand.
IAM isn’t enough by itself
Identity and Access Management (IAM) establishes who users are and grants baseline access across apps and systems. But IAM doesn’t govern how elevated access is requested, approved, used, recorded, and closed—that’s Privileged Access Management (PAM).
Small and mid-sized businesses (SMBs) face the same cybersecurity threats as large enterprises—with fewer resources to fight back. One compromised admin account can unlock an entire environment. That’s why PAM is no longer a luxury. It’s a foundation.
It doesn’t have to be complex or costly. Today’s PAM solutions can be deployed quickly and scaled easily—giving businesses real protection without slowing down operations.
What PAM actually governs
PAM isn’t theory—it’s a set of concrete, verifiable controls:
- Vaulting and rotation: Securely store and automatically rotate sensitive credentials.
- Privileged account discovery: Find unmanaged or forgotten admin accounts.
- Approvals and workflows: Make access intentional, time-bound, and traceable.
- Session recording: Capture every privileged action for accountability.
These controls turn privileged access from risky exceptions into short, auditable events.
How PAM fits alongside IAM
Think of Identity and Access Management (IAM) as your trust fabric: it authenticates users (who they are) and authorizes access (what they can do).
PAM builds on that trust by controlling how elevated access is requested, approved, used, and ended.
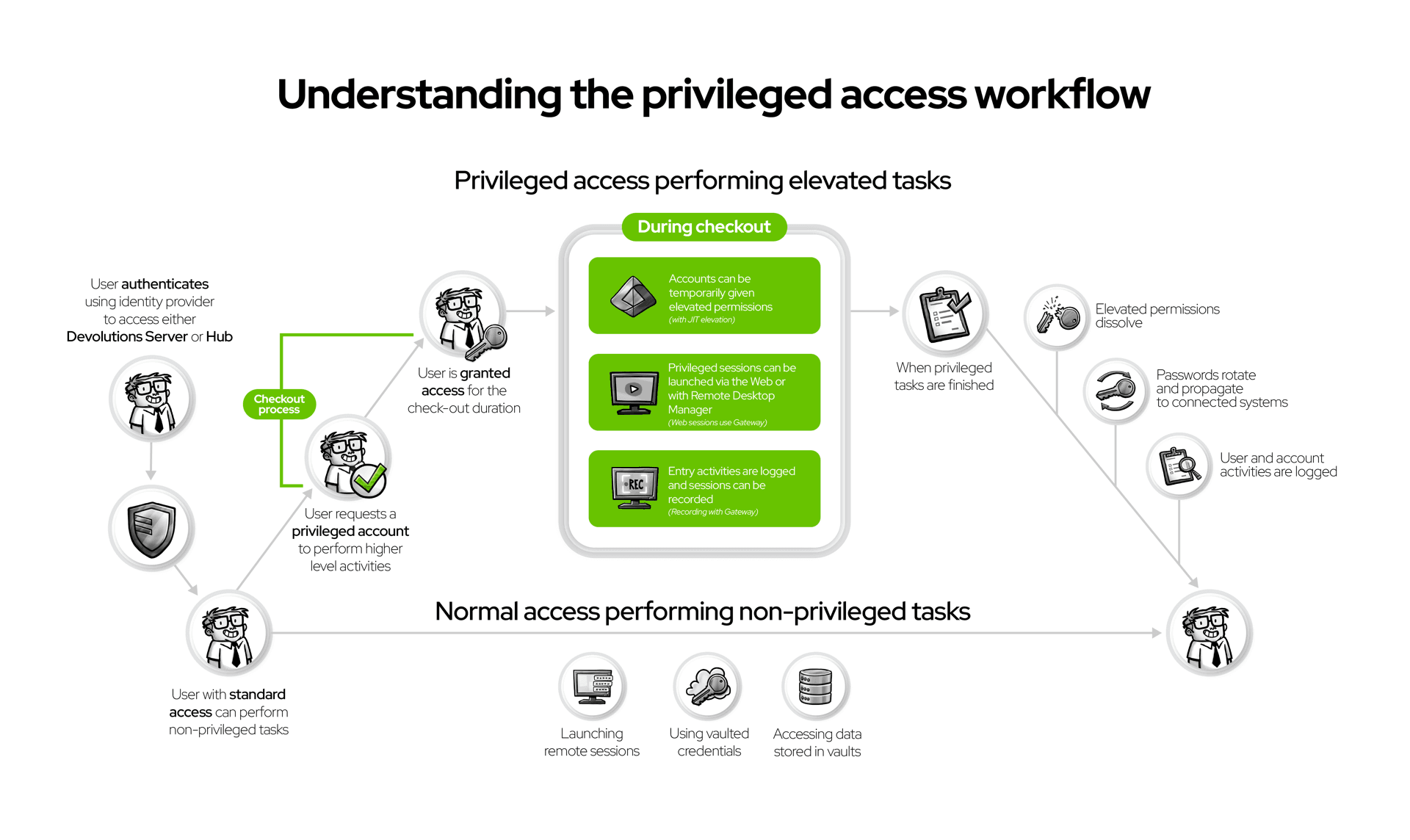
A typical flow looks like this:
- A technician authenticates through IAM (directory + MFA).
- They request privileged access; a policy determines the approval path.
- Sessions start without exposing credentials (they’re vaulted).
- All session activity is recorded and linked to the request.
- When finished, credentials rotate automatically.
Each step produces evidence for audits, insurance reviews, and internal investigations. Together, IAM + PAM deliver identity, intent, and accountability.
Common concerns during PAM adoption
We hear questions and concerns about PAM implementation all the time. Here’s how modern PAM makes the answers simple.
“We’ll slow down.”
Not if it’s done right. Lightweight, time-boxed approvals keep work moving while restoring intent and accountability.
“We already use a password manager.”
Great—that’s step one! PAM goes further by adding context and control: approvals, credential rotation after use, and session recording. Those controls turn convenience into compliance.
“We don’t know where to start.”
Start small and visible. Choose 10–20 high-risk accounts (like domain admins, local server admins, or service accounts). Apply vaulting, rotation, approvals, and session recording. Expand from there.
Pro Tip: Focus first on what would cause the biggest problem if compromised—then prove quick wins to build momentum.
Where Devolutions fits in this landscape
If IAM is your trust fabric, Devolutions PAM is the governance layer that makes privileged work intentional, observable, and short-lived. It delivers the four controls discussed—vaulting & rotation, privileged discovery, approvals/workflows, and session recording—in a package designed for SMBs and mid-market teams.
Why teams choose Devolutions:
- Foundation-first features: The essential PAM controls are built in.
- Affordable: Enterprise-grade protection at the best price in the market - $50 USD/user per month.
- Fast deployment: Get up and running in hours, not months.
- Flexible options: Customize approval workflows to fit seamlessly into your existing processes—without adding friction or extra steps—with our cloud-hosted (Devolutions Hub) and self-hosted (Devolutions Server) deployment options.
- Seamless integration: With Remote Desktop Manager and Devolutions Gateway, you can launch RDP or SSH sessions without exposing passwords—every request, approval, and rotation is logged automatically.
With Devolutions, PAM isn’t a massive project—it’s a fast win that strengthens your foundation.
Ready to see it in your environment?
Start with a small, high-impact scope (10–20 accounts). Measure vaulting, approvals, and session coverage. Then expand confidently.
Evaluate the four core controls in your own environment. Start small, measure results, and scale at your own pace.
