A practical path to PAM: Five quick wins for lean IT teams

Matt Miller
November 10, 2025
Even small IT teams face enterprise-level risks. Privileged accounts — the ones with admin rights or access to critical systems — are often the biggest blind spot.
The good news? You don’t need months or a massive budget to fix it. With the right Privileged Access Management (PAM) approach, you can deploy practical controls in hours and start seeing results right away.
Here’s how to build early momentum with five quick wins that just work.
Quick win #1: Get eyes on privileged accounts
If you can’t see it, you can’t secure it. Start by shining a light on the identities that matter most — the accounts with keys to the kingdom.
Run a privileged account discovery scan across domains, servers, cloud apps, network devices, and critical SaaS roles. Tag each by tier or risk level, then enroll the riskiest accounts into your PAM vault to begin governing, rotating, and auditing them.
Once your discovery process is automated, any new privileged account that appears will be brought under policy quickly — no more unmanaged, forgotten, or orphaned accounts.
The result: visibility and control over the accounts that matter most.
Quick win #2: Limit password access through credential injection
Copy-paste credentials? Sticky notes? Chats with passwords?
Time to retire those habits. By centralizing credentials and using role-based access control (RBAC), you can limit password visibility while still allowing sessions to launch automatically through credential injection. That means your team works as usual — just without ever seeing the passwords.
Enable automatic password rotation on check-in or on a schedule, so the credential used at 10:00 becomes invalid by 10:20. Over time, reuse windows shrink and lateral movement becomes nearly impossible.
The result: better security, no extra steps, and no workflow friction.
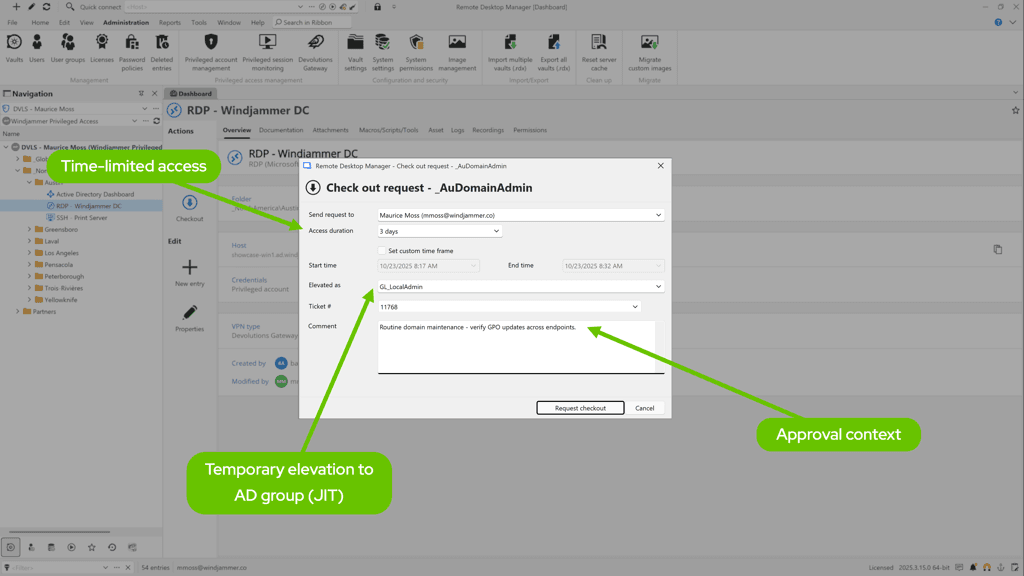
Quick win #3: Simplify elevation with lightweight approvals
Approvals shouldn’t slow you down — they should make privileged work intentional.
Implement time-boxed approvals for high-risk accounts. Each request includes a reason and (optionally) a ticket ID, creating a clear link between access and work performed. To keep things moving, set up your PAM to notify multiple approvers simultaneously during working hours.
The result: fast, traceable elevation that balances agility with accountability.
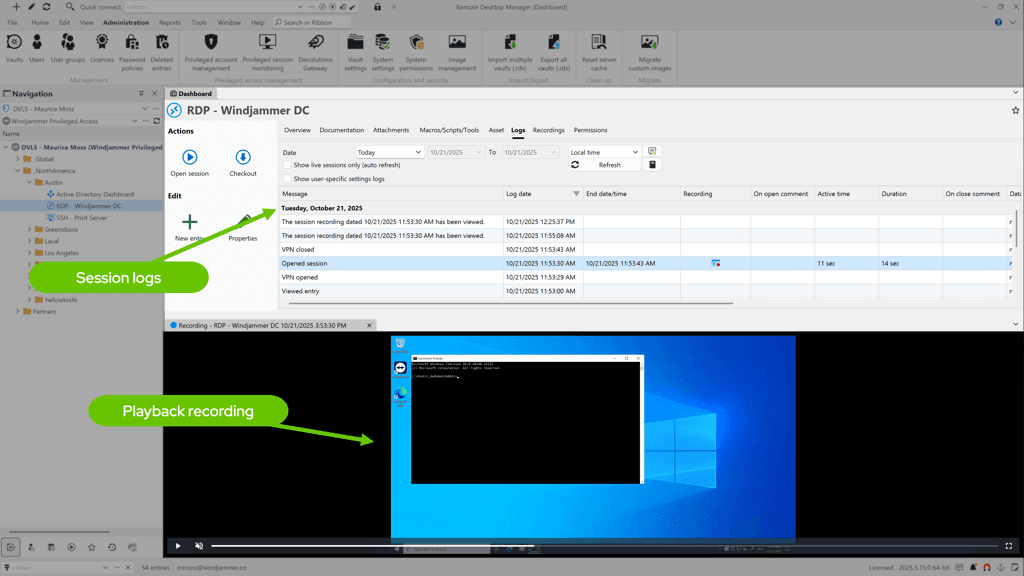
Quick win #4: Turn trust into evidence with session recording
When systems misbehave — or auditors come calling — memory isn’t enough.
Enable session recording for RDP and SSH on privileged accounts to create an auditable chain of custody from request to rotation. In minutes, you’ll know who did what, when, and why — without digging through multiple logs.
The result: stronger incident response, smoother audits, and peace of mind.
Quick win #5: Start small with a two-week pilot
PAM adoption doesn’t have to be all-or-nothing. You can achieve measurable success in just two weeks.
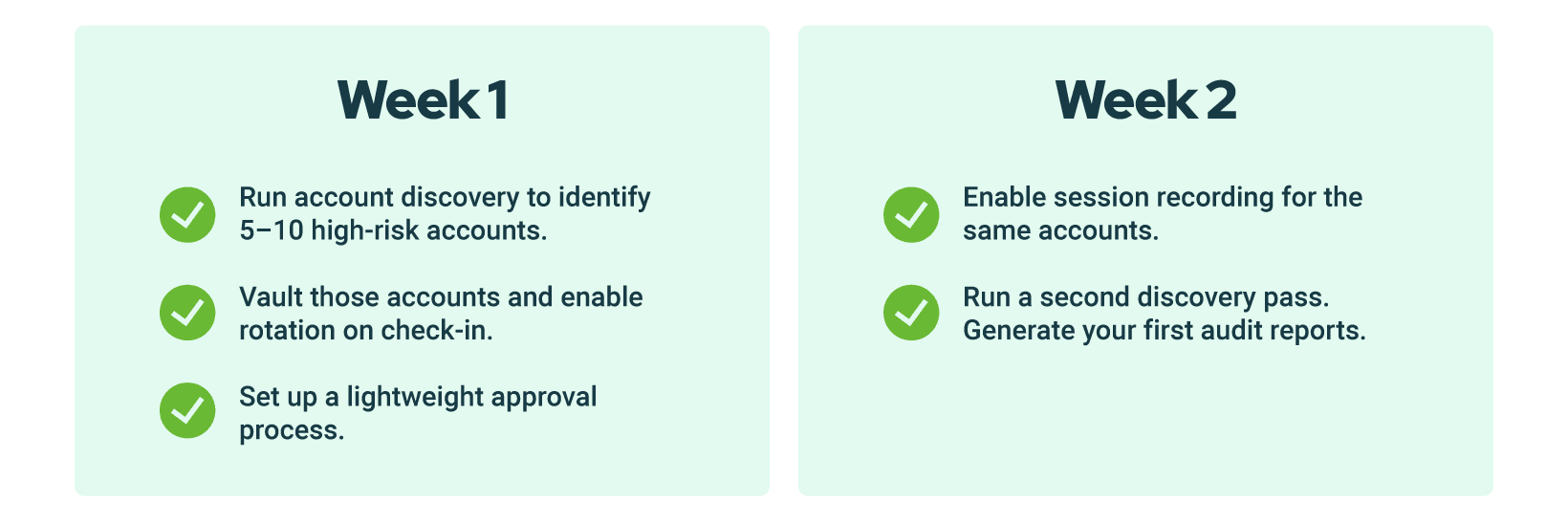
You’ll have working guardrails, measurable results, and proof for stakeholders — all within days, not months.
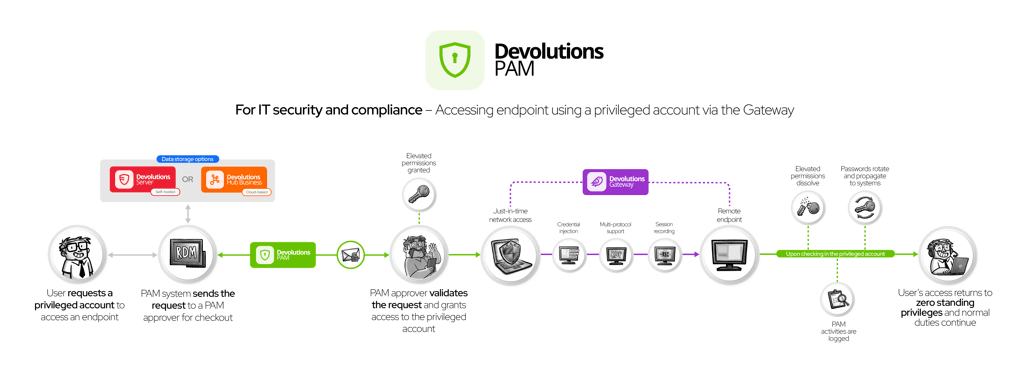
How Remote Desktop Manager & Devolutions Gateway Work with Devolutions PAM
Everything above can be achieved without changing how your team works. Devolutions PAM manages discovery, vaulting, rotation, approvals, and recording behind the scenes.
Using Remote Desktop Manager (RDM) as your main interface, you request approval for a credential checkout. Once approved, Devolutions Gateway brokers the connection (RDP, SSH, etc.), performs credential injection, and ensures the underlying credentials are never exposed. Your admins get seamless access. Your auditors get full traceability. Everyone wins.
Common Concerns
“Won’t approvals slow us down?”
Not when they’re lightweight and time-boxed. Most teams meet their SLAs with ease once the workflow fits naturally into daily operations.
“We already use a password manager.”
That’s a great start for credential hygiene and sharing. Devolutions PAM adds governance — approvals, rotation after use, and recording — turning access into an auditable path.
“Do we have to migrate everything?”
No. Start small with 5–10 accounts. Prove an audit win within two weeks, then expand gradually with discovery and policy coverage.
Try it in your environment
You don’t need months or consultants to see results.
Deploy Devolutions PAM in hours, test it with your own workflows, and measure the impact.
You’ll see how foundation-first features, flexible deployment, and best-in-market pricing make PAM something that just works — for every team size.
Start small, measure, expand — see how fast PAM can work for you.
