From everyday IT tasks to mission-critical demands
Seamlessly scale your operations with one powerful integrated platform. Your business evolves. Your platform should too. From simple password management to advanced PAM deployments, we’ve got everything you need to grow — all in one place.
Discover our solution packages!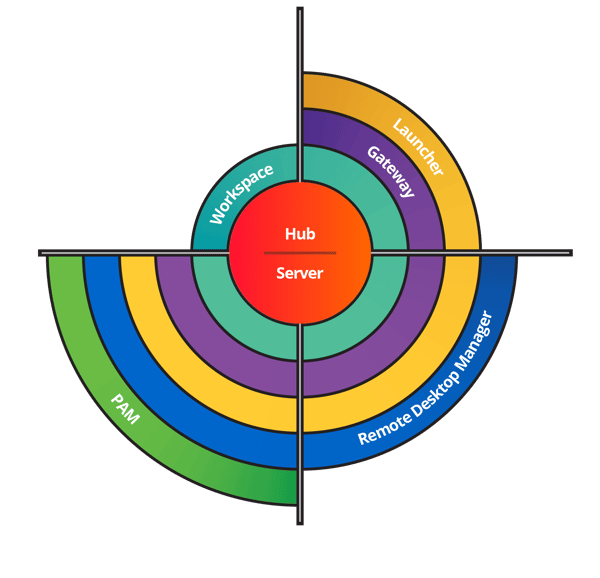
Solutions | Devolutions

Workforce password management
For business users and non-technical staff

Remote access management
For external users, vendors, and IT consultants working from outside of your private network

Remote desktop management & IT operations
For IT professionals, system administrators, network administrators, and helpdesk technicians

Privileged access management
For organizations with privileged users and accounts needing advanced PAM capabilities

Workforce password management
Designed for business users and non-technical staff, workforce password management simplifies credential management across teams and devices while ensuring security policies are enforced. Being able to securely store and retrieve shared credentials reduces password fatigue, enabling seamless authentication workflows without IT overhead.
Included products

Remote access management
Tailored for external users, vendors, and IT consultants, remote access management provides just-in-time access to critical resources without exposing the network. It replaces traditional VPNs with a secure and efficient alternative and ensures visibility over all external connections.
Included products

Remote desktop management & IT operations
Built for IT professionals, system administrators, and helpdesk technicians, remote connection management centralizes all remote connections into a single platform. It enhances operational efficiency while securing access to infrastructure across diverse environments.
Included products







Privileged access management
Designed for privileged users requiring advanced PAM capabilities, this solution safeguards administrative credentials and enforces the principle of least privilege. It mitigates credential-based threats through automated password rotation and just-in-time privilege elevation.
Included products








