Small teams don’t need a maze of security tooling. They need guardrails that deploy fast and are hard to bypass. That’s the promise of JIT in an IT-led PAM program: Grant exactly the rights needed, only for the time they’re needed—then revoke them automatically. In the Devolutions stack, PAM is the engine that enforces JIT; RDM and Gateway streamline requesting, launching, and recording—but PAM can also enforce JIT on its own.
Try it in your environment
Stand up Devolutions PAM in the cloud (Devolutions Hub Business) or on your local server (Devolutions Server) and run the JIT flow in RDM. You’ll see how quickly privileged work becomes intentional, observable, and short-lived, without disrupting daily operations. At the best-in-market pricing for small teams, capable of delivering enterprise-grade outcomes.
Turn privilege into a time-bound, auditable asset
Traditional least privilege trims entitlements, but standing permissions still sit around waiting to be abused. JIT goes further: access is requested, time-boxed, and then removed automatically, with no grace periods. This aligns with Zero Standing Privilege (ZSP): no permanent admin rights, only short-lived access when needed. In the Devolutions model, JIT can cover both “who can become privileged” and “how that privilege is used,” with automatic revocation on expiry. Controlled elevation that doesn’t slow the team down.
Why it matters: You reduce windows of opportunity for attackers, cut lateral-movement risk, and turn every elevation into an auditable, short-lived event.
Day-to-day JIT with RDM + Gateway
Here’s what governed elevation looks like when it’s embedded in the tools admins already use:
- Request in RDM with a reason (and ticket).
- Approve a time-boxed window (e.g., 15/60 minutes)—it expires by itself.
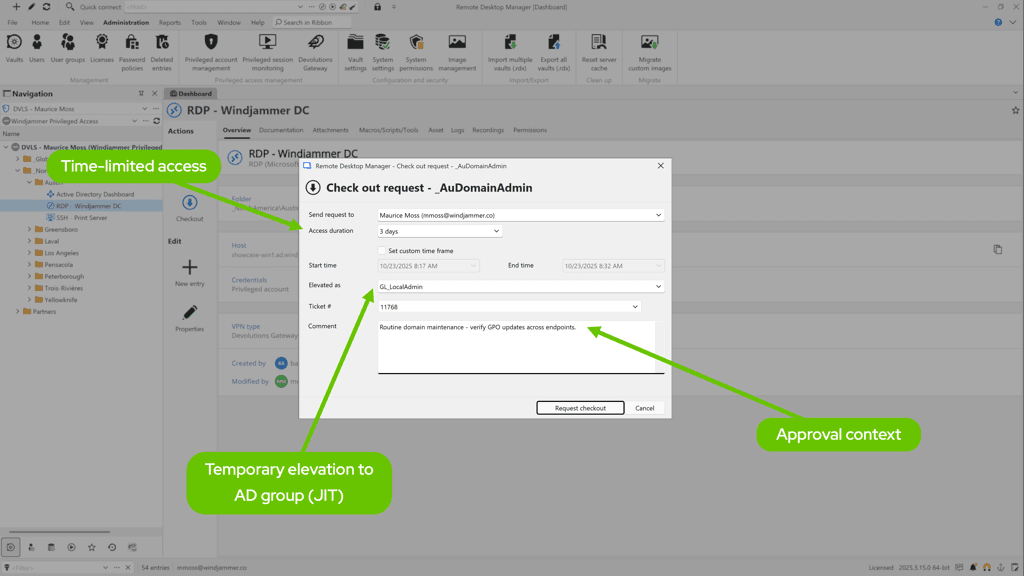
- Launch via Devolutions Gateway with credential injection; passwords aren’t exposed to the user.
- Record the privileged session (RDP/SSH) and tie it to the request.
- Revoke/Rotate on check-in or timeout—access ends, credentials change, and the trail is complete.
Elevation is intentional, traceable, and fast enough to use every time.
JIT elevation & JIT provisioning
JIT elevation: Briefly grant higher permissions to an existing identity for a defined task/window, then auto-revoke.
JIT provisioning: Provision short-lived access tied to a request window and remove it on schedule, with no manual cleanup. In Devolutions PAM, this can mean creating a dedicated account for the task, time-boxing it, then revoking access and rotating the password at the end of the session. Both eliminate standing privilege; choose the pattern that fits your workflow.
Where remote desktop management fits (and why it’s a force multiplier)
Where operation turns policy into practice
Generally, PAM focuses on the credential: Who can use it, for how long, and under what approval. Remote desktop management adds the “how it’s used” layer without slowing admins down. Requests happen in RDM, policy decides approvals, and the data source controls which sessions a user can launch. Credential injection keeps technicians from ever viewing raw passwords, and Devolutions Gateway handles the connection path end-to-end, so sessions traverse networks cleanly and consistently. Because the guardrails live inside the daily toolset, adoption rises. RDM keeps work moving, while PAM governs the credentials and approvals behind every session.
Approvals that match real work
Approvals shouldn’t feel like a detour. Inside RDM, requests come in and are routed to approvers based on established policy. Windows are preset or customized, and responses are sent. Approved sessions are recorded and tied to the request and approval for a clear evidence trail. When the window ends, access ends. No grace periods, and no “I forgot to remove the user” surprises.
Fast, auditable elevation becomes the default, not the exception.
Reporting & risk: Show your work (and your wins)
Auditors want proof, not promises. With Devolutions PAM, your evidence pack can include: the request, the approval trail, the session data or recording (RDP/SSH), and rotation/revocation events—so the story is clear from end to end.
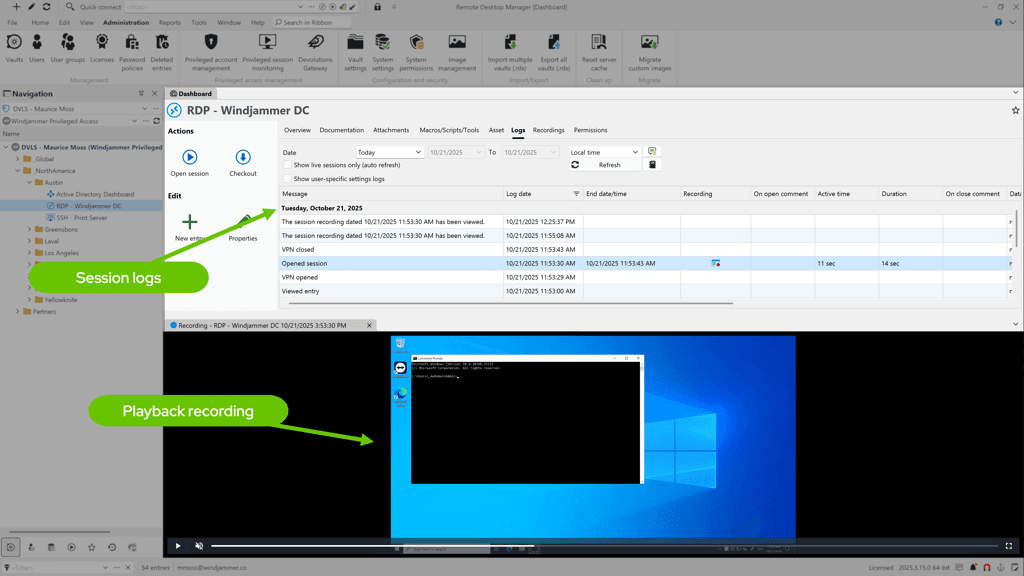
Recent updates also streamline this workflow and make governance easier to demonstrate (e.g., tying tickets to activity and strengthening the “who/what/when/why” linkages in reports).
Reconstruct what happened in minutes, with objective metrics for coverage and SLAs.
What we’re working on
We’re continuing to invest in:
- Broader provider coverage: Expanding the list of managed provider types so more of your IT ecosystem can be discovered and governed by PAM, and align with the Principle of Least Privilege (PoLP).
- Finer-grained permissions: Increasing permission flexibility and granularity on privileged accounts and PAM vaults to better enforce ZSP, enable separation of duties, and fit more org models (including MSP scenarios).
And we’re exploring:
- Browser-based ergonomics via Workspace Browser Extension: Evaluating ways to bring select PAM actions into the browser—think reviewing/approving requests or triggering rotations—so simple tasks can happen with less context switching. We’ll share specifics as designs mature.
Start a free 30-day PAM trial or try Devolutions PAM in a free, browser-based lab session to see how we’re helping IT pros achieve great PAM coverage with less standing access in their organizations.
 Matt Miller
Matt Miller

 Coralie Lemasson
Coralie Lemasson
