Hello Devolutions community!
January is that special time of year when we all take a hard look at our habits, make ambitious resolutions… and quietly hope this is finally the year they stick. (Yes, that includes security projects that have been “on the roadmap” since at least three budget cycles.)
To kick off 2026, our January poll asked a very direct question: What are your privileged access management (PAM) resolutions in 2026?
As expected, the answers were honest, practical, and very relatable. Let’s dig in.
PAM: from “no-brainer” to “maybe this is the year”
One strong theme that emerged is that, for many, PAM is no longer a “nice to have.”
Several community members see PAM as table stakes for doing things right. The sentiment was clear: if privileged access is managed using best practices, there shouldn’t be much left to “resolve” next year — it simply becomes part of how security is done.
“We’re not there yet” (and that’s OK)
At the same time, a few respondents were refreshingly candid: PAM isn’t on their immediate radar.
The most common reason? Company size. Some smaller teams feel that adopting a PAM solution would be overkill for now, or that their environment simply hasn’t reached that level of complexity yet.
This perspective is important. Security maturity doesn’t look the same everywhere, and not every organization starts from the same place.
Convincing management and securing budget
Another recurring resolution was less technical — and very real: getting buy-in.
Several respondents hope 2026 will be the year they can:
- convince leadership that PAM is necessary,
- secure a dedicated budget,
- and finally centralize the management of privileged accounts.
For many IT and security professionals, the challenge isn’t understanding the risk, it’s making that risk visible and actionable for decision-makers.
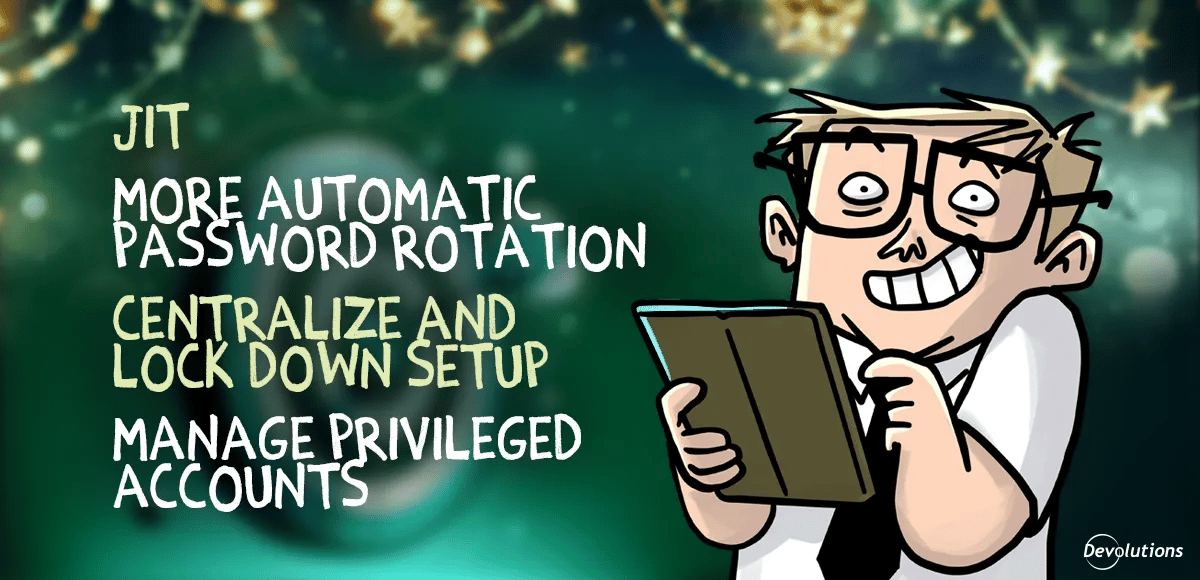
Feature-driven goals: JIT and automation
Finally, a few responses zoomed in on specific PAM capabilities, including:
- Just-in-time (JIT) access
- More automated password rotation
- Centralizing and locking down privileged setups
These answers typically came from organizations that already understand PAM’s value and are looking to level up, not start from scratch.
The winners
Now for the fun part! Two lucky poll participants have been randomly selected to win a $25 Amazon gift card. Congratulations to Dan Tapley and Matthew Roslevich! Please email asguerin@devolutions.net to claim your prize.
What’s next?
A new poll is already on the way, and it will continue exploring how the community approaches security in the real world, not just in theory. Stay tuned!

 Steven Lafortune
Steven Lafortune