These days, a company can get by without a phone number. Some don’t even need a physical location. But not having a searchable website? That’s unthinkable!
However, in June, that’s exactly what happened to devolutions.net. For five chaotic days, our entire domain was delisted from Bing — the default search engine for Microsoft Edge. Anyone looking for us saw third-party sites instead of ours.
Here is the inside story of what happened: a massive, human-operated spam campaign that slipped past our defenses, overwhelmed our forum, and quietly poisoned our search presence on Bing — and how we fought to get it back.
So it begins…
At around 2:00 AM EST on June 19, 2025, our team began noticing a sharp rise in forum activity — and not in a good way. By the time we got fully involved, over 5,000 spam messages had been created. These posts contained scam content: links to shady websites and phone numbers that, when called, led to scammers posing as tech support.
Our forum’s database struggled under the load. Performance degraded rapidly, to the point of near-unresponsiveness. What made this campaign different from most others was that it was human-driven. These weren’t bots. Real people manually registered over 500 accounts, bypassing all our automated protections — including Cloudflare Turnstile CAPTCHA, which is not intended to block real humans.
OSINT insights
Our OSINT team quickly confirmed that this wasn’t an isolated attack. The same group was posting across a wide array of public platforms — DeviantArt, Bluesky, forums, classified ads, and more. We stopped counting after 15 unique external websites. The goal appeared to be SEO abuse — creating backlink trails to improve the search engine visibility of scam sites and services.
We tracked over 400 unique IPs, mostly from India, including several residential ISPs. A large part of the attack also used VPN services like Private Internet Access. We even called two of the scam phone numbers for verification:
- One claimed to be Xerox support and prompted us to install remote assistance software.
- The second was tied to an "Expedia offer," but the agent had no idea what Expedia was — and still wanted remote access.
Internal side effects
During the cleanup, we noticed something odd: our internal chatbot started responding with content from the spam posts. Typing "hi" triggered scammy replies. This confirmed a real risk: LLM contamination from public content, especially in environments where user posts are indexed or mirrored internally.
Becoming a ghost on Bing
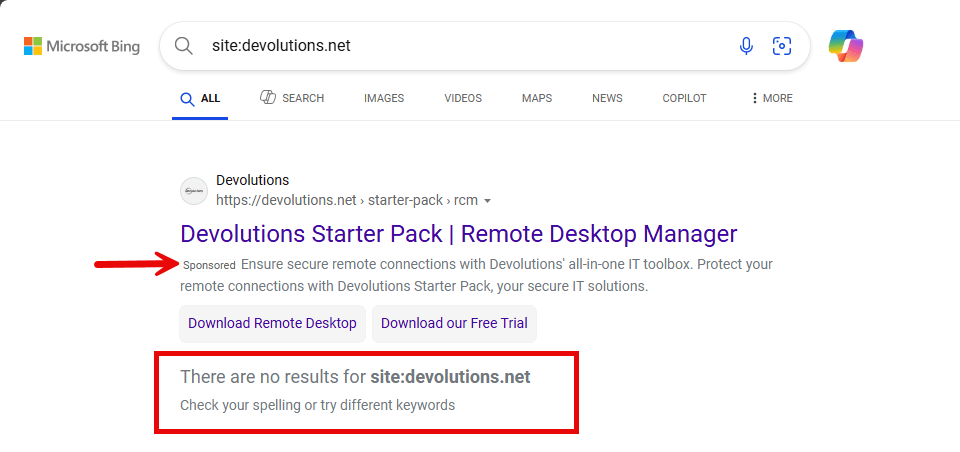
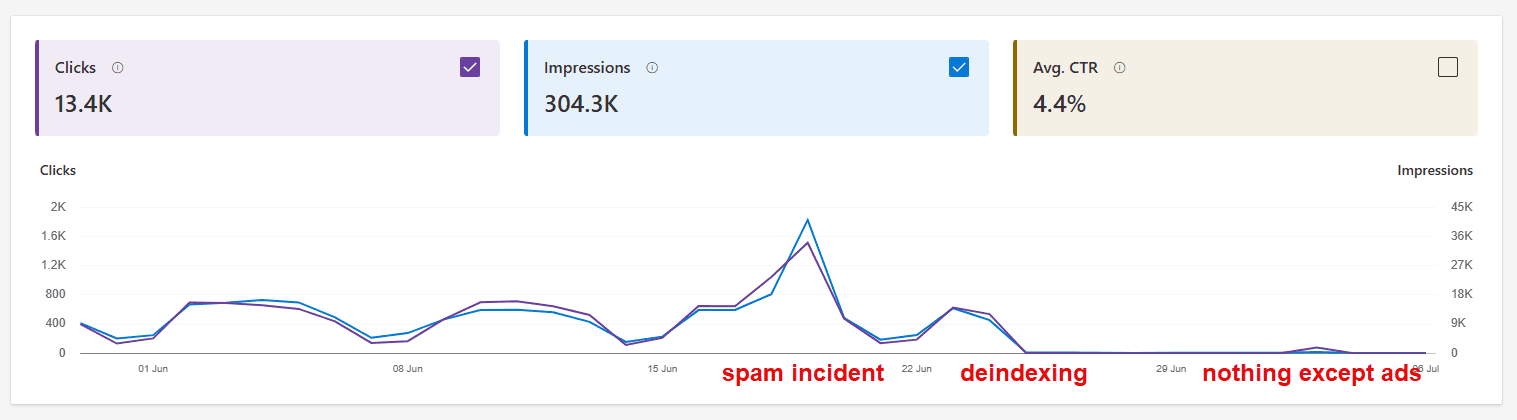
A few days later, we noticed a major drop in web traffic coming from Bing. In Bing Webmaster Tools, everything looked normal — except for a strange sitemap error. We originally thought it was an issue with the tooling, until we realized the data was correct: almost nobody was seeing our content. The few remaining impressions and clicks were solely from paid advertisements, as forum.devolutions.net and devolutions.net had been fully deindexed from Bing:
We had effectively become invisible — anybody searching for Devolutions on Bing would never find us, only third-party sites talking about Devolutions. This is a big deal because Microsoft Edge on Windows uses Bing by default.
To make matters worse, ChatGPT uses Bing behind the scenes in SearchGPT, so being a ghost on Bing has a more profound impact. Surprisingly, ChatGPT would still find our website, but there's no telling for how long.
During the spam incident, we had a lot of impressions for searches like "expedia customer service" pointing to the spam on our forum, so we can only guess that the Bing algorithms flagged forum.devolutions.net and its parent domain, devolutions.net as undesirable. The scammers used the notoriety of our website to push their fake customer service information in search results, but it simply got us banned in the end.
What we did
- Blocked forum posts at the WAF level by 10:30 AM on June 19
- Added a moderation step for all first-time forum posts
- Purged all spam posts via direct DB cleanup
- Documented attack vectors via OSINT and threat intel
- Confirmed domain delisting from Bing
- Contacted Bing support
The last part — contacting Bing support — was the most stressful. There's a support form you can fill out in Bing Webmaster Tools, but once you have a ticket number, all you can do is wait. Surprisingly, there doesn’t seem to be a way to pay for premium support when it comes to Bing. We would have gladly paid to escalate the issue!
Without naming names (to avoid giving others the idea), we managed to contact someone from the Bing team during their vacation through LinkedIn DMs. This got our ticket some attention internally, and a few days later we got a response that the ban had been lifted. Still, we were helpless about the situation for much longer than felt comfortable.
Timeline (EST)
Here is a timeline of the events, starting from the initial impact through to the final resolution:
| Time | Event |
|---|---|
| ~02:00 AM | Sudden spike in spam on the community forum begins |
| 03:00–05:00 AM | Over 5,000 scam posts published; database begins to choke |
| 10:30 AM | WAF rule deployed to block all forum post submissions |
| ~12:00 PM | First moderation steps added for posts |
| +2 days | Drop in Bing traffic observed and investigated |
| +3 days | Domain confirmed delisted from Bing search index; Contacted Bing support |
| + 5 days | Confirmation from Bing that domain relisted to search index |
What we learned
- Human attacks don’t care about your CAPTCHA. Automated protections were bypassed with ease. Manual review was necessary.
- Bad data pollutes everything — including AI. Internal AI systems must have safeguards against the ingestion of bad or unmoderated data.
- Search engine trust is fragile. A wave of low-quality content can quickly get you delisted — without warning.
- IP and keyword filtering are weak against real attackers. These sit low on the Pyramid of Pain and are easy to evade.
- Don’t underestimate Bing just because Google exists. You only realize the value of something once you lose it — pay attention to Bing.
Final thoughts
This incident reminded us that security isn’t just about stopping bots — it’s about thinking like your adversary, especially when they’re human. If you're operating a public platform, it's worth asking: “What happens when the bad guys aren’t automated?” You might end up learning the hard way, just like we did.


 Steven Lafortune
Steven Lafortune
